Every time you connect to the internet, your IP address leaves a trace revealing small details about your personal information. The FBI’s Internet Crime Complaint Center (IC3) reported $16.6 billion in losses from internet crimes, proof that even something as simple as an IP address can lead to real harm.
You’ve probably asked yourself, “What can someone do with your IP address?” and the answer will surprise you. In this post, we’ll explain how cybercriminals get it, the risks it creates, and the steps you can take to protect yourself, so you avoid dark web hackers stealing and selling your data.
Need support after a scam? Join our community today.
What Can Someone Do With Your IP Address?
With just an IP address, someone can guess your general location, map your provider, and track when you’re most active online. That’s enough to build a profile, direct DDoS traffic at your connection, or restrict content by region. It isn’t a direct way into your device, but it can be the starting point for targeted hacking attempts.
1. Approximate Location
Your IP can point to your general location, such as your country, state, or city, using databases that link IP ranges to specific regions. It doesn’t show your exact address, but it narrows the area for anyone trying to confirm your connection.
- Example: Someone could see that a connection comes from the Chicago area and use that detail to send phishing emails or scams that look like they come from local companies.
2. Internet Provider and Connection Type
An IP address also reveals your internet service provider (ISP) and whether you’re browsing from a home, business, or mobile network. That information can help someone estimate how secure your connection might be.
- Example: If they detect that you’re on a residential Comcast network, they could try to attack your router or slow your internet by limiting your connection speed.
3. Online Activity and Browsing Habits
By linking your IP with traffic records, others can figure out when you’re most active online, the websites you often visit, or the services where you log in regularly. Over time, this forms a character profile that can be used for tracking or targeted ads.
- Example: If an IP shows regular access to streaming platforms at night, a hacker could take advantage of that pattern to launch attacks when you’re connected.
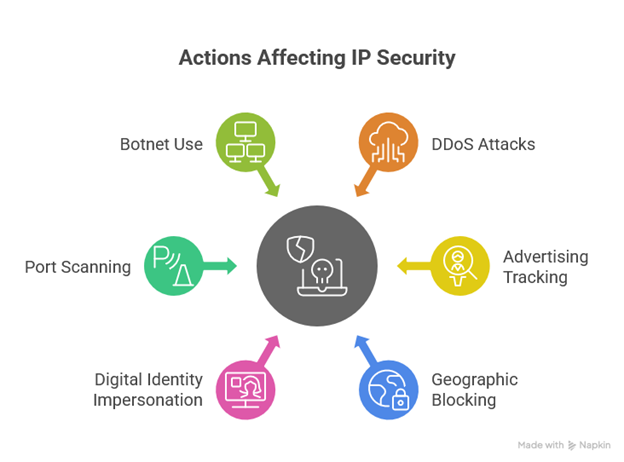
What Actions Can Someone Take With Your IP?
Once someone gets your IP address, they can use it in different ways that affect your connection, privacy, and online reputation. Here are the most common actions and what they can cause:
1. DDoS Attacks
A flood of bogus requests overwhelms your network until it slows to a crawl or goes offline. This tactic typically targets gamers, small teams, and creators.
- Example: During an eSports match, an attacker uses your IP to knock your connection offline and kick you out of the server.
2. Advertising Tracking
Sites and services can tie activity to your IP to build a profile with searches, time patterns, and preferences. That profile supports personalized ads and may be shared with other parties.
- Example: If you often browse tech shops, you start seeing computer and gadget ads across many sites.
3. Geographic Blocking
Platforms read your IP to recognize your country and restrict content by region. Some governments apply similar methods to limit access to information.
- Example: When you travel outside the United States, your usual Netflix or Hulu catalog changes because your IP signals a different region.
4. Digital Identity Impersonation
Illicit traffic can be routed through your IP, so actions look like they came from you, unauthorized downloads, or probing of other systems.
- Example: If your IP appears in spam or attack logs, your ISP may throttle or suspend your connection while the issue is reviewed.
5. Port Scanning
Attackers probe open ports on your network to spot weak or poorly configured services. A single gap can expose devices in your home.
- Example: An open management port on your router can give access to a security camera or a personal server without your knowledge.
6. Sale Or Use In Botnets
Big lists of IP addresses feed spam runs, crypto-mining, and coordinated attacks. On anonymous forums, brokers buy and rent these lists by the thousand, allowing threat actors to rotate addresses quickly and launch new spam or DDoS campaigns within minutes.
- Example: Your IP ends up in a botnet queue and gets used in a global spam campaign while you keep browsing as usual.
Have questions about dealing with scams? Contact us for support.
How Hackers Can Get Your IP Address?
Now, if you’re asking what someone can do with your IP address, it’s worth seeing how it’s obtained. Your IP travels with every visit and click, so different services can see it along the way. Here are some of the most commonly used methods:
- Web browsing: Sites you visit log the IP of the device that connects. It’s routine and used for basic operation and diagnostics.
- Tracked emails: Some messages include a tiny image; when you open the email, that image loads from a server and records your IP with a time stamp.
- Chats, online games, and calls: During matches or video calls, your IP can be visible to the platform and, in some cases, to other participants, depending on how the service works.
- P2P and torrents: When you share files, your IP appears in the public list of peers. Anyone in that pool can see it and link it to the shared content.
Advanced Or Malicious Methods
- Phishing links: A fake “verification” page logs your IP the moment it loads. If you submit details, the risk grows.
- Ads or downloads with hidden code: Tampered banners or files collect your IP when they load or install.
- Poorly protected routers: If your router uses an easy password or weak settings, automated bots try guesses until they get in and view your public IP.
- Social engineering: Someone poses as support, sends a “help” link, or asks you to install a tool that quietly sends back your IP.
👉Check how to check if your computer has a virus, spot early signs that often follow IP-based targeting, such as sudden slowdowns, pop-ups, or logins you don’t recognize.
What Can’t Be Done With Just Your IP?
Having your IP address doesn’t give someone a doorway into your device. It’s an online identifier used to route traffic, but on its own, it doesn’t open your files or accounts. Without a live weakness to exploit, an IP is only a reference. Here is what a hacker can’t do if they get your IP:
1. No Access To Your Files Or Passwords
An IP contains no login details and doesn’t connect anyone to your folders, email, or accounts. To reach that level, a WiFi hacker would need malware or a phishing lure.
- Example: Knowing your IP isn’t enough to view your photos or documents unless you install a malicious file.
2. No Exact Home Address
Public geolocation tools point to a general area, not a street address. The customer records that would pinpoint it are held by ISPs and aren’t exposed through your IP alone.
- Example: Someone might see a Texas location, but not your street or house number.
3. No Hacking Without A Weakness
An IP provides no permissions or credentials. A real break-in requires exploiting a flaw or an open port on your network.
- Example: With updates in place and a firewall active, the IP by itself doesn’t present a path in.
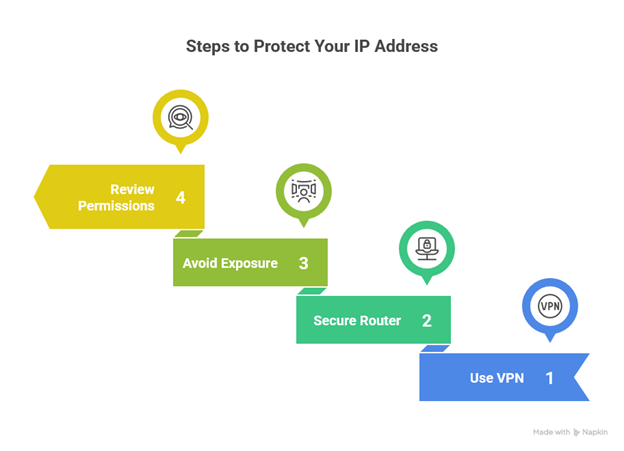
How To Protect Your IP Address And Stay Safe?
Protecting your IP lowers risk and makes it harder for others to build a profile or disrupt your connection. Here are simple steps you can apply right away to close off common entry points:
1. Use A Reliable VPN
- Encrypt your traffic and mask your IP: A VPN routes your connection through its servers, so websites see the VPN’s address instead of yours.
- Free vs. paid: Free plans often cap data, have fewer locations, and come with unclear terms. Paid services usually provide better speed, independent audits, and responsive support.
- Check “no-log” claims and legal base: Favor providers audited by third parties and based in locations with strong privacy laws.
2. Set Up Your Router And Firewall The Right Way
- Change default passwords: Use long, unique credentials and turn off WPS if you don’t need it.
- Keep firmware updated: Enable automatic updates when available, and review the router settings monthly.
- Close unused ports: Disable UPnP unless it’s required, and remove old port-forwarding rules.
- Keep the firewall on: Use both the router and operating system firewalls to filter outside traffic.
4. Avoid Unnecessary Exposure
- Don’t post your IP publicly: Skip screenshots or forum posts that reveal it.
- Be careful on public Wi-Fi: Connect through a VPN, turn off file sharing, and stick to HTTPS.
- Review app and extension permissions: Remove tools you don’t use and limit network or tracking access.
Learn and Take Control of Your IP and Privacy
Your IP address reveals signals about you, so reduce exposure before someone uses it. If you’re wondering “what can someone do with your IP address?”, the picture is clear: tracking, service blocks, and DDoS attacks. Turn on a VPN, secure your router, and keep your firewall active.
Want to go further? Check your social footprint: fake Facebook profiles and impersonation scams often tie in with IP-based scams. At Cryptoscam Defense Network, we see these patterns every day. Take control now, review permissions, block suspicious accounts, and keep your online setup protected.
✅ Download our Fraud Report Toolkit to easily collect, organize, and report scam cases, with dropdowns for scam types, payment methods, platforms, and direct links to agencies like the FTC, FBI, IC3, CFPB, BBB, and more.
We Want To Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Frequently Asked Questions About What Can Someone Do With Your IP Address
Is It Illegal To Find Someone Else’s IP?
Seeing an IP that’s visible on a site or connection is usually not a crime, but using it to harass, attack, or impersonate can bring legal penalties. Avoid collecting or posting other people’s IPs. If something crosses the line, report it to your ISP and the platform.
How Can I Tell If My IP Was Hacked?
The IP itself isn’t hacked; the connection gets used fraudulently. Watch for persistent slowness, sudden blocks, or login attempts you don’t recognize. Check blacklists, run DNS/WebRTC leak tests, update your router passwords, and review the router logs.
How Often Does My IP Change?
Home plans often use dynamic IPs that can change after a modem reboot or based on ISP policy. Business setups or remote-access needs may rely on static IPs. If you want frequent rotation, talk to your ISP or use a VPN.