Your email connects many parts of your digital life. It stores personal details, links to your accounts, and is often used to confirm your identity. Because of this, it is a frequent target in cyber incidents. In 2025, 61% of data breaches involved compromised emails, according to Huntress.
What can scammer do with your email? In this post, you’ll learn about the risks that come with it and the simple steps you can take to keep your information safe. Let’s go through the dangers clearly so you know what to watch for.
Need support after a scam? Join our community today.
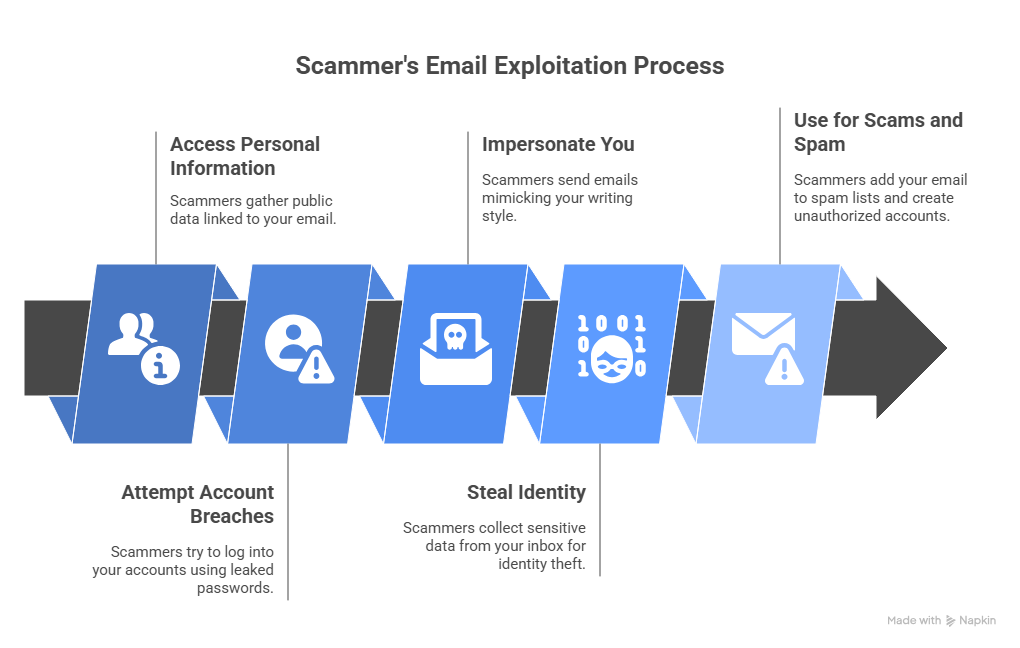
What Can Scammers Do With Your Email?
Scammers can use your email in more ways than most people expect, and not all of them are obvious at first. Some actions are annoying, while others can lead to serious security problems. Here are the most common risks you should know about:
1. Access personal information linked to your email
With your email, scammers can look for public information connected to it, such as your full name, social profiles, or old accounts you forgot about. This gives them clues about your habits, interests, and the services you use.
- Example: They might find your Instagram and target you with a fake login page.
2. Try to break into your online accounts
Your email is often the key to resetting passwords. If scammers combine your email with leaked passwords from past data breaches, they may attempt to log in to your banking, shopping, or social media accounts.
- Example: They could test a password you used on an old website to access your Amazon account.
3. Impersonate you and contact your friends or coworkers
Scammers may send emails that look exactly like something you would write. They can copy your writing style, use your name, and even reply to old messages found in your inbox. This makes the message feel real to the person receiving it.
- Example: Someone you know might get a fake email from “you” asking for money or personal info.
4. Steal your identity using data found in your inbox
Some inboxes contain invoices, documents, or sensitive messages. If scammers access these, they may collect enough details to perform identity theft or open accounts in your name.
- Example: They might find your full address and ID details in an old rental application.
5. Use your email for scams, spam, or unwanted sign-ups
Your email can be added to spam lists or used to create accounts without your permission. This fills your inbox with unwanted messages and can expose you to more phishing attacks.
- Example: Suddenly, you start getting dozens of emails from strange services you never signed up for.
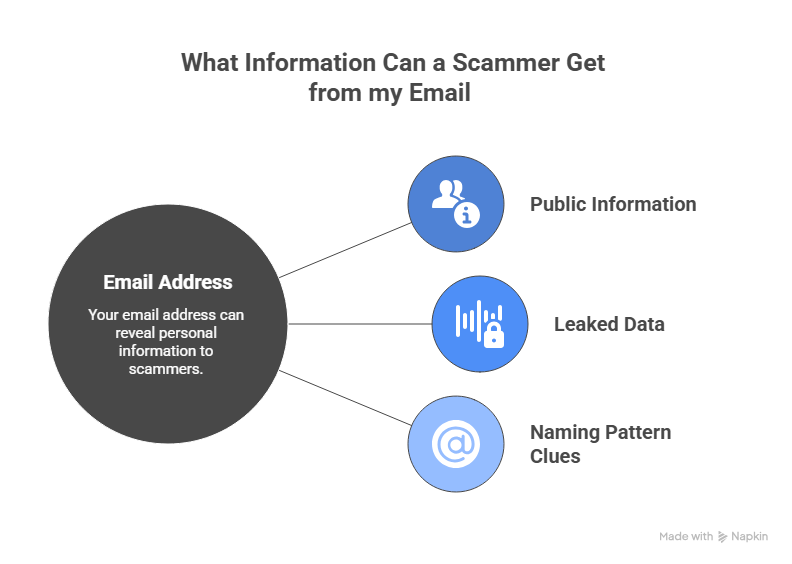
What Information Can a Scammer Get From Your Email Address?
Your email can reveal more than just your username. A scammer can combine public data, old accounts, and leaked information to build a clearer picture of who you are. This helps them create more targeted attacks. Here are the main types of information a scammer can find:
- Public information from social media and websites: If your email is linked to public profiles, a scammer can find your full name, photos, job details, city, or old posts. This gives them context about your life and makes their messages more convincing.
- Data leaked in past breaches: If your email appeared in a data breach, a scammer may find old passwords, phone numbers, or partial personal information connected to your account.
- Clues from your email naming pattern: Some email addresses include personal details, such as your birth year, full name, or workplace. These small clues help scammers guess passwords, answer security questions, or identify other accounts you might have.
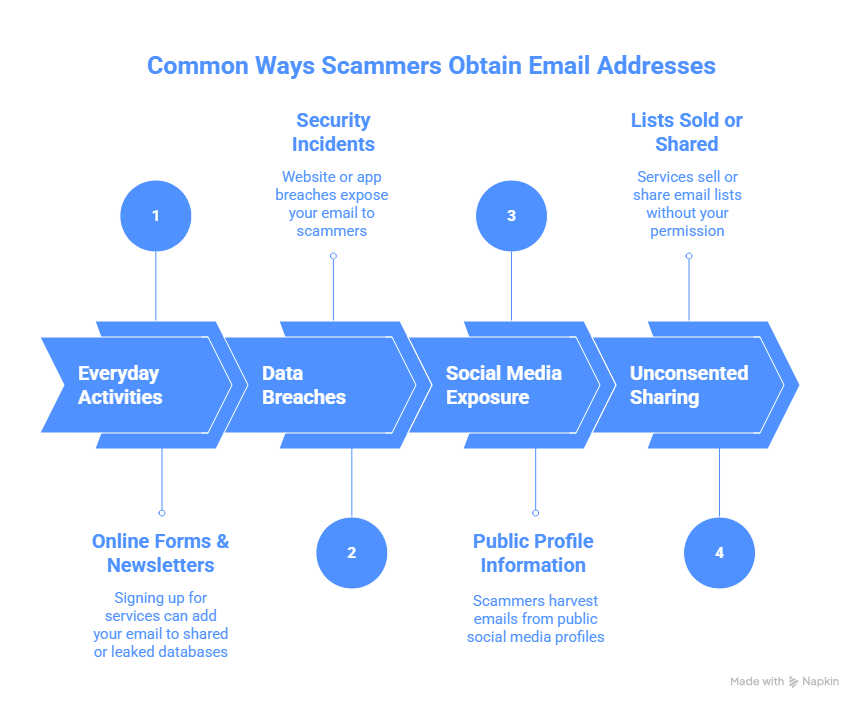
How Scammers Usually Get Your Email?
A scammer doesn’t always need special tools or skills to find your email. In many cases, it comes from everyday actions, public sources, or leaks you might not even be aware of. Here’s how they often get access to your address:
- Online forms and newsletters: When you sign up for newsletters, discounts, or online services, your email can end up in large databases. Some of these lists get shared, sold, or leaked, making it easy for scammers to access them.
- Data breaches: Websites and apps sometimes suffer security incidents. If your email was part of a breach, it may appear on lists that scammers use to run phishing attacks or try password combinations.
- Social media exposure: Many profiles display email addresses for contact or business inquiries. A scammer can take this information directly from your public profile and use it to send targeted messages.
- Lists sold or shared without your consent: Some services collect emails and pass them to third parties. Over time, these lists circulate through different companies, giving scammers new ways to reach you even if you never interacted with them.
Have questions about dealing with scams? Contact us for support.
How Can You Tell If a Scammer Is Using Your Email?
A scammer does not need full access to your inbox to cause trouble. Small signs often appear first, and noticing them early can prevent bigger problems. If you see any of the following situations, it may be a sign that a scammer is trying to use your email:
| Warning Sign | What It Means |
| Password reset notifications you didn’t request | A scammer may be trying to access one of your accounts by triggering a password reset. |
| Emails sent from your account without your knowledge | Someone may be impersonating you or testing access to your inbox. |
| Login alerts from unknown devices or locations | A scammer may be trying to use your credentials on different platforms. |
Real Case: Large-Scale Phishing Attack Shows How Scammers Use Emails
Recent security news helps illustrate how far a scammer can go once they have an email address. A report from The Hacker News described a large-scale phishing attack targeting hotel systems.
How the Attack Worked
The attackers used a malware tool called PureRAT to compromise internal networks by sending convincing phishing emails to employees.
The victims received emails that looked normal, but once a single person clicked, the scammers gained access to credentials, documents, and communication tools inside the organization. This allowed them to move through different parts of the company and reach sensitive systems.
Here are the key points from the incident:
- The attack started with a simple phishing email that encouraged employees to click on a fake link.
- Once inside, scammers collected account credentials, giving them access to more systems.
- The malware hid inside regular traffic, making it harder to detect at first.
- The attackers used the stolen information to impersonate employees and send more phishing messages.
- The entire attack was possible because a single email was compromised.
This real case shows how quickly a scammer can escalate an attack, even inside large organizations. It’s a clear reminder that protecting your email is not just about avoiding spam; it’s about preventing access to the tools and information that keep your digital life safe.
How to Protect Your Email From Scammers?
A scammer depends on weak passwords, exposed information, or unsafe habits to reach your inbox. Small changes in the way you manage your email can reduce the risk. These steps are simple to follow and make your account much harder to target:
- Use a strong password and enable MFA: A long, unique password makes it harder for scammers to guess or reuse old credentials. Adding multi-factor authentication gives you an extra layer of protection even if your password is exposed.
- Keep your main email private: Use your primary email only for important accounts. For newsletters, online stores, and sign-ups, a separate email reduces exposure and limits where your main address appears.
- Create a second email for sign-ups: A dedicated email for downloads, coupons, or free trials keeps your main inbox clean and avoids unnecessary risks if that secondary address ends up in a leaked list.
- Avoid oversharing online: If your email appears on public profiles or websites, a scammer can easily pick it up. Review what is visible and remove anything that does not need to be publicly accessible.
- Be cautious with links and unexpected messages: Scammers often use urgent or surprising messages to make you click without thinking. Always check the sender, preview links, and avoid downloading unknown files.
Protect Yourself When Scammers Misuse Your Email With Cryptoscam’s Guidance
Email security is about staying informed and responding early when something doesn’t look right. When you learn how scammers use email, it is easier to protect your information and spot unusual activity before it grows into something serious.
At Cryptoscam Defense Network, we focus on helping you stay safe online through clear guidance and reliable tools. As your trusted resource for online fraud prevention, our mission is to give you the knowledge and support you need to stay safe in the modern digital environment.
✅ Download our Fraud Report Toolkit to easily collect, organize, and report scam cases, with dropdowns for scam types, payment methods, platforms, and direct links to agencies like the FTC, FBI IC3, CFPB, BBB, and more.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.
Frequently Asked Questions (FAQs) About What a Scammer Can Do With Your Email
Can a scammer access my bank account with my email?
Not directly. But if your email is connected to your banking profile and your password has been exposed, a scammer can try to reset your login or bypass security steps. Strong passwords and MFA help prevent this.
Can a scammer track my location through my email?
Not directly. However, if your email is connected to social media or public profiles that share your city or workplace, a scammer can piece together general location details.
Can a scammer use my email to create new accounts?
Yes. Some platforms allow sign-ups without verification. A scammer may use your email to open accounts you don’t recognize, which can lead to spam or misuse of your information.
Photos via Freepik.




