The elements of fraud can be challenging to detect because deception often blends into everyday situations. It doesn’t always appear dangerous—until the consequences are already happening. Many people struggle to identify the warning signs or understand how these schemes work.
In this post, we’ll show what the key elements of fraud are, how they differ from a scam, and how to recognize them in everyday situations. We’ll also explain what steps to take if you’re ever involved in one and review common types of fraud along with the U.S. laws created to address them.
Need support after a scam? Join our community today.
What Are the Elements of Fraud?
When we talk about elements of fraud, we’re referring to the minimum conditions that need to be in place for fraud to be identified and proven in a legal setting. It’s not just about feeling deceived—it’s about showing that there was a planned action with the intent to cause harm. Here are the 4 elements of fraud:
1. False Representation of a Relevant Fact
False representation is an element of fraud that involves presenting false information as if it were true. This goes beyond exaggerations or opinions—it’s about deliberately misleading someone to gain their trust or influence their decisions.
Examples
- A seller claims a product is new when it’s already been used.
- Someone pretends to work for a company they’re not affiliated with.
2. Knowledge That the Information Is False
Knowledge of falsity is an element of fraud that occurs when the person making the false claim knows it’s untrue. That intent might not be obvious right away, but it’s there from the moment they decide to twist the truth to gain something.
Examples
- Posting a fake job offer, knowing it doesn’t exist.
- Saying they have a license or credentials that were never earned.
3. Intent to Deceive and Gain a Benefit
Intent to deceive is an element of fraud that reflects a purposeful effort to mislead someone for personal gain. The person acts with full awareness, aiming to obtain money, sensitive information, or access to something they’re not entitled to.
Examples
- Asking for a fee to apply for a job that doesn’t exist.
- Requesting sensitive information to misuse it later.
4. Loss or Damage Caused by the Fraud
Loss or damage is an element of fraud that confirms the impact of the deception. For fraud to be established, the victim must suffer a specific loss—whether financial, personal, or related to time or opportunity.
Examples
- Paying money under pretenses.
- Losing access to private information.
- Missing a legitimate opportunity due to a fraudulent offer.
What is the Difference Between Fraud and Scam?
Fraud and scam are terms that are often used interchangeably, but they refer to different types of deceptive actions. Knowing how to tell them apart can define the legal steps you take if you decide to report what happened.
Fraud usually involves a planned setup or manipulated information. A scam, on the other hand, tends to rely on social engineering tricks such as emotional manipulation or false promises.
Here’s a quick comparison of their key differences:
Difference Between Fraud and Scam
| Aspect | Fraud | Scam |
| Structure | Involves a planned setup and detailed execution | Often spontaneous or improvised |
| Evidence | Usually includes fake documents, contracts, or false identities | Often lacks physical evidence or formal documentation |
| Method | Uses systems, paperwork, or falsified information | Relies on words, persuasion, or emotional appeal |
| Legal Approach | Involves the structured elements of fraud, which can be legally proven | May be harder to prove due to lack of traceable proof |
| Example | A fake website selling products that don’t exist | A message asking for money due to a made-up emergency |
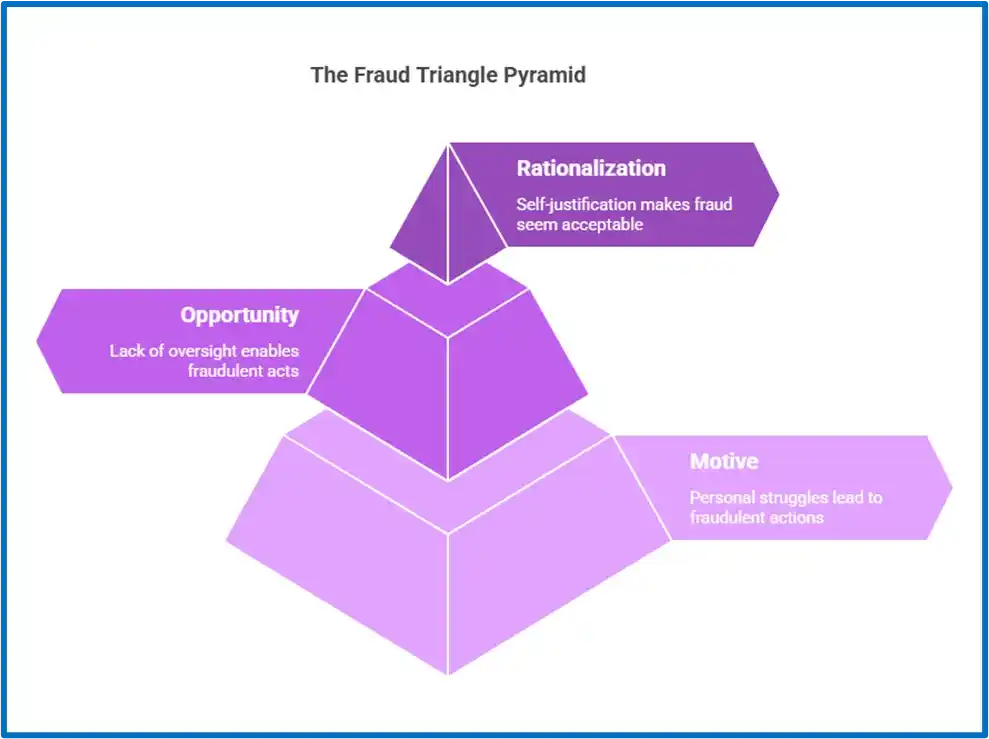
What Is the Fraud Triangle?
The fraud triangle is a model developed by criminologist Donald Cressey to explain the three common factors that often lead a person to commit fraud. These factors are: motive, opportunity, and rationalization.
When they appear together, they create the conditions in which fraudulent behavior becomes more likely. Each factor plays a specific role:
1. Motive
A motive is the personal pressure or need that pushes someone toward fraud. It can stem from financial problems, family issues, or other difficult situations. In these cases, the person may feel trapped and see fraud as the only possible solution.
2. Opportunity
Opportunity refers to the situation or environment that allows fraud to happen. This includes lack of supervision, easy access to money or data, or weak internal controls. When no one is monitoring, the chance to act dishonestly increases.
3. Rationalization
Rationalization is the internal process the person uses to justify the act. They may believe their actions are temporary or harmless or that they deserve what they’re taking. These thoughts reduce guilt and make it easier to continue.
Example of the Fraud Triangle
In business environments, the fraud triangle becomes a useful tool to identify early warning signs. For example, if an employee is facing personal pressure, has access to resources without supervision, and begins to justify questionable actions, all three factors of the model are present. This combination increases the risk of fraud.
According to the 2022 Report to the Nations, 42% of occupational fraud cases are detected through internal tips. Recognizing these patterns early can help protect your team and organization before the elements of fraud turn into real damage.
Have questions about dealing with scams? Contact us for support.
What Are the Types of Fraud?
There are different types of fraud, but identifying which one you’re facing is essential. It influences how the deception unfolds, how you detect it, and what steps you can take in response.
In general, there are three main categories. Each one involves the elements of fraud, but they appear in different ways depending on the situation:
1. Individual Fraud
This type of fraud is committed by a person acting alone, without any connection to a company or institution. It often takes advantage of internet anonymity or informal spaces to gain trust quickly.
- Example: Someone creates a fake store on social media, uploads attractive product photos, replies to messages politely, and offers “unique” prices. People pay, but the product never arrives.
- What Causes It? From the start, the goal is clear: pretend to run a real business to get money or personal data. It’s one of the most frequent types of fraud and also one of the easiest to replicate.
2. Internal Fraud Within an Organization
This happens when someone inside a company abuses their role to commit dishonest actions. It could be someone manipulating financial data, misusing internal systems, or accessing confidential information.
- Example: A finance employee alters reports, transfers money to personal accounts, or justifies fake payments.
- What Causes It? This type of fraud often combines three key elements: lack of control or oversight (opportunity), personal pressure such as debt (motive), and internal justifications like “they owe me” (rationalization). It’s especially damaging when the person holds a high-level position.
And this isn’t just something that happens in big companies. Small business fraud is becoming more common, mainly because smaller teams don’t always have strong controls in place. When trust takes the place of proper oversight, fraud can slip by until the damage is already done.
3. External Fraud Against Companies or Institutions
In this case, the fraud is committed by someone outside the organization who has gathered enough information or resources to appear legitimate. This type of fraud is often more complex and harder to detect without proper controls, and by the time it’s identified, the financial damage has usually already been done.
- Example: Someone pretends to be a regular supplier and sends a fake invoice with altered bank details. Since everything seems in order, the payment goes through—and ends up in the fraudster’s account.
- What Causes It? This type of fraud is typically about getting quick access to money without raising suspicion. The attacker studies the company, copies real details, and appears familiar.
Another example is digital wallet fraud, where a scammer gains access to payment systems or impersonates employees through phishing, malware, or fake support calls.
Which Laws Protect Against Fraud in the United States?
Understanding the elements of fraud helps you recognize when something feels off and gives you a starting point if you ever need to take legal action. In the U.S., several laws offer protection for both individuals and organizations affected by different types of fraud.
Here are a few of the most relevant ones:
1. Major Fraud Act (18 USC § 1031)
This law applies when someone commits fraud against the U.S. government. For example, a company might secure a public contract using false documents or manipulating information to receive federal funds.
2. Foreign Corrupt Practices Act (FCPA, 1977)
This one deals with business activity beyond the United States. It was created to prevent U.S. companies from offering payments or engaging in dishonest practices abroad. If someone lies or manipulates data to close a deal in another country, they could face charges under this law.
3. Millennium Challenge Act (MCC, 2003)
While its main focus is international economic development, this act includes tools to address corruption and misuse of public funds. It also promotes greater transparency in countries that receive U.S. financial aid.
4. Computer Fraud and Abuse Act (18 U.S.C. § 1030)
This law applies when someone gains unauthorized access to a computer or digital system. If your account was hacked, your data was taken, or you suspect misuse of your online information, this law offers a legal way to take action.
5. Identity Theft and Assumption Deterrence Act (18 U.S.C. § 1028)
If someone used your Social Security number or banking details without your consent, this law addresses that. It penalizes those who steal and use personal data and supports victims in reporting identity fraud.
6. Sarbanes-Oxley Act (2002)
Created in response to major corporate scandals, this law sets strict standards for how public companies handle financial reporting. It also helps prevent accounting fraud that can impact employees, customers, or investors.
Identify Elements of Fraud with the Cryptoscam Defense Network
When you understand the elements of fraud, it becomes easier to spot the risks before they grow. A fake invoice, an employee manipulating reports, or a merchant who isn’t who they say they are—these aren’t random events; they follow patterns.
At Cryptoscam Defense Network, we help businesses stay ahead of online threats—not just crypto cases of fraud but all kinds of digital deception. If you’ve spotted warning signs or want to strengthen your internal controls, we’re here to guide you through every step. You don’t have to deal with it alone. ¡Join us!
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future frauds.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.
Photo via Pixabay.







