Data leaks don’t just happen to big companies: they can affect anyone who’s ever created an online account, signed up for a newsletter, or saved a password in a browser. Personal details like your email, phone number, or login credentials might already be circulating online without you realizing it.
Even if you’re careful when using the internet, data breaches still represent a constant threat, as shown by Statista, which reported 3,158 officially recorded cases in 2024. This post answers the question “How to check if my data was breached?” using verified tools, how to interpret the results, and what steps to take to protect your accounts from future exposure.
Need support after a scam? Join our community today.
How to Check If My Data Was Breached: 4 Reliable Tools
If your data was breached, the fastest way to confirm it is to check through trusted online tools. These sites match your email or credentials against verified breach databases and quickly show if your data appears in any known leaks. Here are the most reliable options, all free and safe to use:
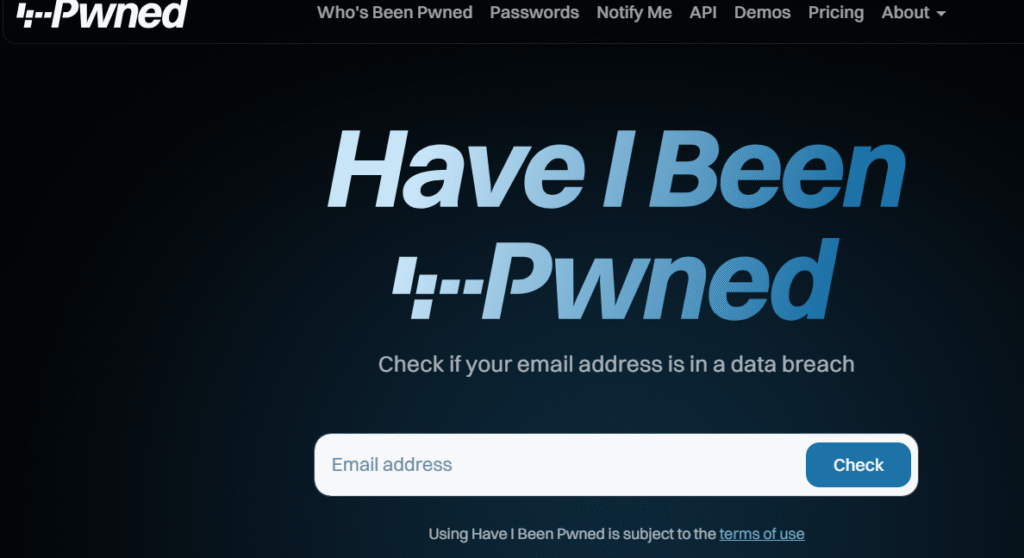
1. Have I Been Pwned
Have I Been Pwned is one of the most respected data breach databases, created by cybersecurity expert Troy Hunt.
How to Use It
- Go to the website and type your email address in the search bar.
- Click “Check” to scan billions of leaked records.
- If your email appears in breaches, the site lists the services affected and the type of data exposed, like passwords or phone numbers.
- If the result is “Good news—no pwnage found”, your address hasn’t been seen in known leaks.
📌 You can also sign up to get a data breach alert if your email appears in future breaches.
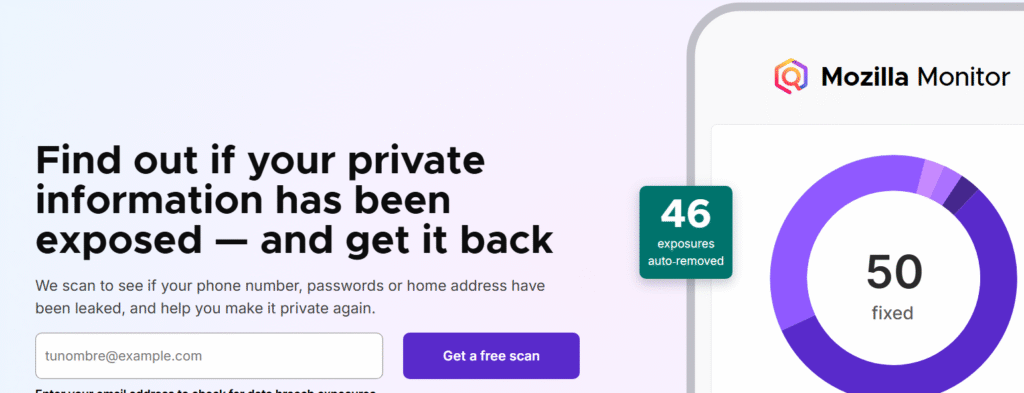
2. Firefox Monitor for Automatic Alerts
Firefox Monitor is a free Mozilla service that alerts users if their online accounts have been compromised in a known data breach.
How to Use It
- Visit the site and click “Check for Breaches”.
- Paste your email to scan for known exposures.
- Sign in with a Mozilla account to receive email alerts if your data appears in new leaks.
- The report shows which sites were breached and when, so you know which accounts to secure first.
📌 Firefox Monitor never stores your password; it only checks your email hash against breach records.
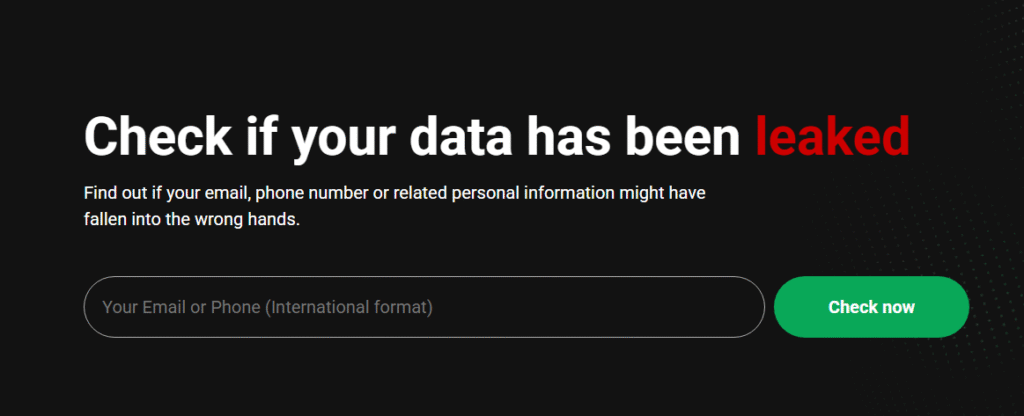
3. Cybernews Data Leak Checker
The Cybernews Data Leak Checker is another reliable source that scans billions of exposed credentials.
How to Use It
- Type your email address in the checker field.
- Click “Check now”.
- Review the results; if a breach is found, Cybernews lists the websites involved and the type of data exposed.
- You can also subscribe to updates to be notified about new breaches.
📌 Cybernews also publishes detailed reports about recent leaks, which add useful background context.
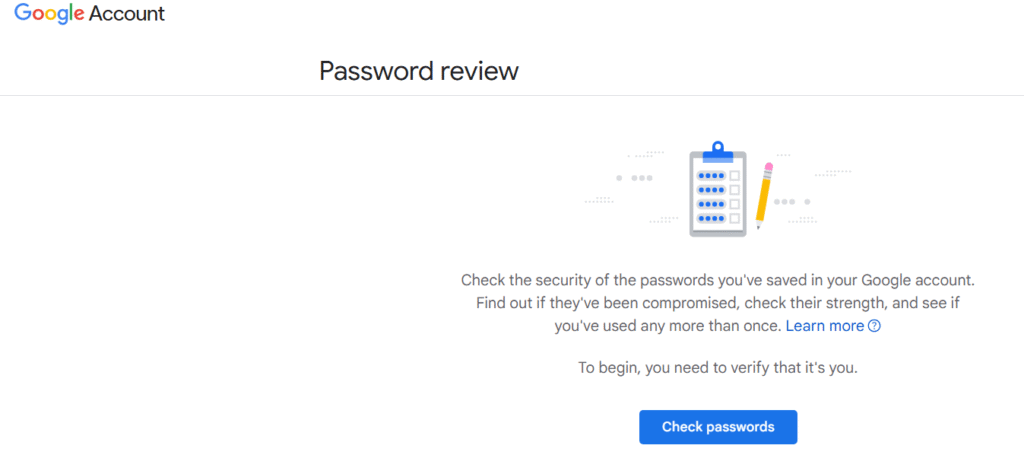
4. Google Password Checkup
If you use Chrome or store passwords in your Google Account, the Google Password Checkup tool can help.
How to Use It
- Log in to your Google Password Manager.
- Click “Check passwords”
- Google compares your saved logins against known data breaches.
- You’ll get a list of compromised, reused, or weak passwords that need updating.
📌 This feature runs automatically if you’ve enabled Chrome’s Password Manager. You’ll see a warning icon when a password has been exposed.
Have questions about dealing with scams? Contact us for support.
How a Data Breach Works
A data breach happens when someone gains access to a system that stores your personal information, usually through one of a few weak points:
- Reused or weak passwords
- Outdated software or unpatched apps
- Malicious links or phishing emails
Once hackers get in, they quietly copy or steal the data, often without you realizing it. Your details can then be sold, traded, or posted online, which is why you might suddenly receive spam, scam messages, or unfamiliar login alerts.
What Are the Most Common Causes of a Data Breach?
Most data breaches are not the result of a single big mistake. They frequently happen when a few little mistakes accumulate, such as a weak password or a missing software update. Catching these early allows you to be safe and react quickly if something goes wrong:
- Phishing emails that trick you into sharing your password: Messages that look like they come from your bank or a delivery service asking you to ‘verify’ your login details. Always check the sender’s address and avoid clicking links in unexpected emails.
- Weak or reused passwords that are easy to guess or crack: Using the same password across multiple accounts means that if one site is compromised, all your accounts could be at risk. Consider using a password manager to create and store unique logins.
- Malware that steals saved logins from your devices: These malicious programs often come from fake downloads or attachments. Keep your antivirus updated and avoid downloading files from unknown sources.
- Outdated or unpatched software: Leaves websites or apps vulnerable. Regularly updating your operating system, browser, and security software helps close those holes before hackers can use them.
- Insider threats: This can happen intentionally or by mistake, when someone within a company leaks or steals data. For this reason, companies should implement strong data-handling policies and restrict access to sensitive information.
What Information Is Usually Exposed?
Not all breaches expose the same kind of information. Some leaks reveal only emails, while others include financial or identity data. Here’s what is most often affected:
| Type of Data | Where It Might Come From |
| Email addresses & passwords | Online accounts, subscriptions |
| Names, phone numbers, addresses | E-commerce sites, social media |
| Payment or banking details | Online stores, payment processors |
| IDs or medical records | Healthcare providers, government databases |
What to Do If Your Data Was Compromised
Prevention starts with small daily habits. Simple steps can stop many breaches before they begin. Follow these steps to reduce your risk if your data was compromised:
1. Change Your Passwords
Start with the affected account and any others using the same password. Choose strong, unique passwords that include a mix of letters, numbers, and symbols. A password manager can help you keep track of them securely. Prioritize email accounts first; many other logins depend on them for password resets.
2. Active Two-Factor Authentication (2FA)
Turn on 2FA wherever possible. This adds a second layer of protection, such as a code sent to your phone or generated by an authentication app, making it much harder for attackers to get in, even if they have your password.
3. Monitor Your Accounts
Keep an eye on your email inbox, bank statements, and credit card activity for unusual transactions or notifications. If something looks off, contact the company or your financial institution immediately.
4. Check for Other Affected Services
Breaches often affect multiple sites that share credentials. Use the same breach-checking tools you tried earlier to see if other accounts are involved. Update those passwords right away.
5. Stay Alert for Phishing Attempts
Attackers may follow up with fake security warnings or “account recovery” emails. Avoid clicking links in unexpected messages and go directly to the official website to verify any alert.
6. Explore Identity Protection Services
If sensitive information, such as your ID number or financial data, was exposed, consider using an identity protection or credit monitoring service. These services can alert you to suspicious activity and help recover your identity if needed.
Reduce Data Breaches with Cryptoscam Defense Network
Good security doesn’t require complex tools, just awareness and simple habits you apply every day. Change weak passwords, stay alert for scams, and keep your software up to date. Protecting your digital life is an ongoing effort, but it’s one that truly pays off.
At Cryptoscam Defense Network, we help you understand and prevent digital threats with knowledge and tools to avoid and reduce digital hazards, enabling the identification of scams, protection of digital wallets, and encouragement of safer online investment practices.
✅ Download our Fraud Report Toolkit to easily collect, organize, and report scam cases, with dropdowns for scam types, payment methods, platforms, and direct links to agencies like the FTC, FBI IC3, CFPB, BBB, and more.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.
Frequently Asked Questions (FAQs) About How to Check if My Data Was Breached
How Can I Tell If an Email About a Breach Is Real?
Scammers frequently send fake alerts to steal your information. Real companies won’t ask for your password by email. To verify a message, go directly to the company’s official website instead of clicking any link in the email.
Should I Delete My Account After a Breach?
Not always. If the company fixes the issue and improves its security, changing your password might be enough. But if you don’t trust how they handle your data, it’s better to delete the account and remove any saved payment information.
How Can I Avoid Future Data Breaches?
To avoid future data breaches, follow these steps:
- Use unique, complex passwords for every account.
- Turn on two-factor authentication whenever possible.
- Keep software and browsers updated to patch vulnerabilities.
- Be cautious with links and attachments in unexpected emails.
- Review your privacy settings on key accounts regularly.
Photos via Freepik.



