Cyberattacks have become faster, more precise, and easier to launch. What once required technical expertise is now available through free tools and malicious code. According to Levelblue, the average ransomware kit costs just $56, and the most popular versions cost as little as $14. This means businesses can be attacked, often without warning.
You need more than a firewall or a long password to protect confidential company information from hackers. You require a system that prevents unauthorized access, detects cyberthreats early, and limits the damage if something goes wrong. In this post, you’ll learn simple strategies and actions that work to protect your business.
Need support after a scam? Join our community today.
Best Practices to Protect Confidential Company Information from Hackers in 2025
To protect confidential company information from hackers, you don’t need a complex setup; you need a few solid practices applied with consistency. These are the 7 most effective steps you can take right now, even without a dedicated IT team.
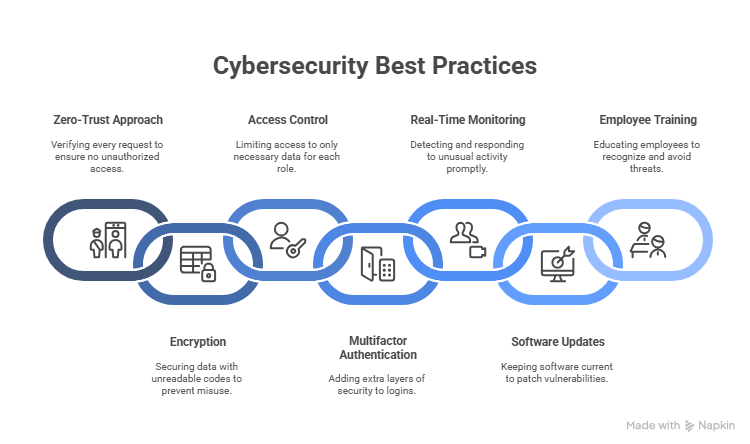
1. Don’t Automatically Trust Anyone or Anything
A zero-trust approach means checking every request, no matter where it comes from. Every user, device, and connection must prove it belongs before gaining access to your systems.
🛡️How to apply it?
- Require user verification for every system or app.
- Use device validation and geolocation controls.
- Remove implicit trust from internal networks.
2. Use Encryption to Keep Your Data Safe Even If It Gets Stolen
Even with strong security in place, files can end up in the wrong hands. Encryption makes sure that, if that happens, the information stays unreadable and useless to attackers. Data should be protected both while it’s stored and while it’s moving between people, apps, or locations.
🛡️How to apply it?
- Choose tools that use AES-256 encryption for stored files and backups.
- Make sure your systems support TLS 1.3 for secure data sharing and communication.
- Turn on full-disk encryption on all company laptops, phones, and USB drives.
3. Give People Access Only to What They Need
Many data breaches happen when an attacker uses one account to reach everything inside a system. That risk drops quickly if permissions are limited. Employees should only be able to open, edit, or share the files and systems needed for their specific tasks. Nothing more.
🛡️How to apply it?
- Define access rules for each department or role.
- Review permissions every quarter.
- Immediately remove access when someone changes roles or leaves the company.
4. Add a Second Step to Every Login
Stolen passwords are still one of the most common causes of data theft. However, with multifactor authentication (MFA), a password alone isn’t enough to obtain entry. Even if a WiFi hacker guesses or steals a password, they won’t pass the second check, like a code from an app or a fingerprint scan.
🛡️How to apply it?
- Turn on MFA for all company accounts: email, storage, HR systems, and admin panels.
- Use app-based or hardware authentication rather than SMS when possible.
- Make MFA required, not optional.
5. Watch for Unusual Activity and Act Quickly
Many companies don’t realize they’ve been attacked until weeks or months later. Real-time monitoring can help you spot unusual behavior early, before damage is done. Things like odd login times, unknown devices, or big file transfers can be signs of a breach in progress.
🛡️How to apply it?
- Use monitoring tools that track system activity.
- Set alerts for things like failed logins, permission changes, or downloads outside business hours.
- Review logs regularly to catch anything automated systems may miss.
6. Keep All Software Updated
Outdated software often contains known weaknesses that hackers specifically look for. The longer those gaps stay open, the higher the risk of an attack. Patching regularly closes those gaps and keeps your systems protected against the most common threats.
🛡️How to apply it?
- Use automatic scanners to identify what needs updating.
- Apply patches as soon as they’re available, especially for servers, apps, and browsers.
- Don’t forget about less obvious tools like printer firmware, plugins, and internal platforms.
7. Teach Your Team What Threats Look Like
Even with strong technical protection, human mistakes can open the door to attacks. That’s why training matters just as much as software. Employees should feel confident in identifying suspicious emails, login pages, and unusual requests. The goal isn’t to scare people, just to prepare them.
🛡️How to apply it?
- Teach how to identify fake login pages and suspicious emails.
- Run internal phishing simulations.
- Share short monthly tips or checklists.
How to Create a Cybersecurity Plan You Can Manage?
You don’t need a complicated setup to protect your company. What you need is a plan that’s clear, realistic, and works with the way your team operates. When it comes to cybersecurity, the best plans are modular and made up of different layers that protect people, data, devices, and access. These layers are easy to change as your business grows.
The table below shows how to break your plan into manageable parts. Each area includes a clear goal and a few simple actions to help you apply it in real life:
| Element | What It Means | How to Apply It |
| Access | Control who can view, edit, or share sensitive information | Assign permissions based on roles. Remove unused accounts. Use MFA for all access points. |
| Devices | Know which computers, phones, or platforms are being used to access company systems | Keep an updated inventory. Apply full-disk encryption. Enforce password and lock screen policies. |
| Data | Understand where your files live, how they move, and who can reach them | Map where files are stored (cloud, local). Disable unnecessary sharing links. Use secure backups. |
| People | Recognize how your team interacts with data—mistakes often come from routine habits | Train employees to detect phishing. Set clear dos and don’ts. Make reporting easy and fast. |
| Visibility & Monitoring | You can’t protect what you can’t see. Your tools should help you track what’s happening inside your systems | Use platforms that log user activity. Set alerts for odd behavior. Review system logs regularly. |
| Simple Rules, Consistently Used | A plan only works if your team follows it | Keep policies short and practical. Share them often. Review them quarterly. |
| Documentation That Works | Your cybersecurity plan should be clear enough for someone new to follow, and useful in case of an incident | Document access rules, escalation steps, and key contacts. Avoid unfamiliar terms. Keep it easy to update. |
Have questions about dealing with scams? Contact us for support.
How to Protect Your Reputation Besides Your Data?
When a company suffers a data breach, the technical damage can be repaired. Files can be recovered, passwords reset, and systems patched. But the trust you lose with clients, partners, and your team is much harder to restore.
Cybersecurity is also brand protection. Clients want to know that you take care of their data. Regulators expect fast, honest action, and employees need to trust that the tools they use each day won’t put them at risk.
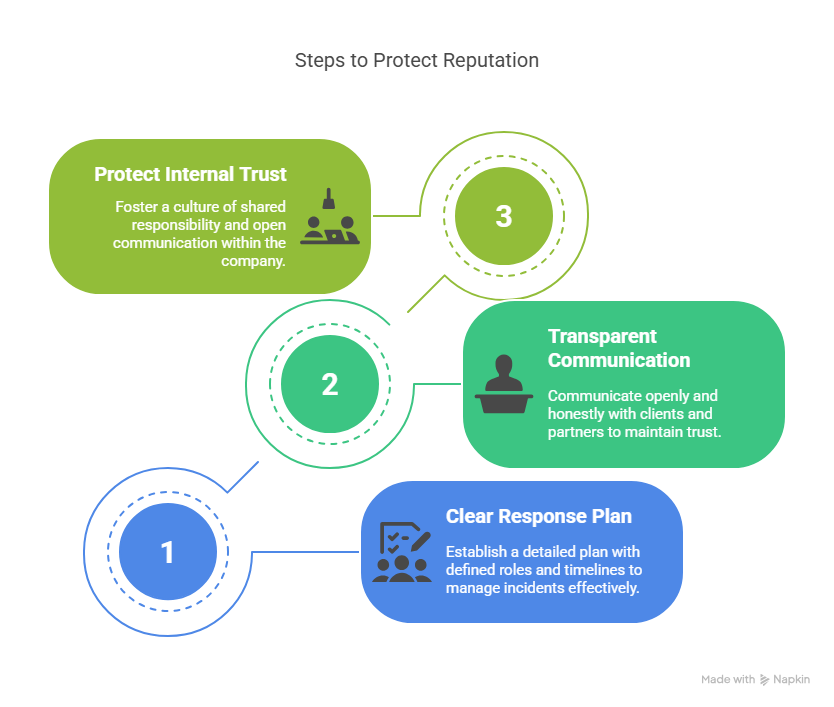
Here’s how to prepare your company to protect its reputation:
1. Have a Clear Response Plan Before Something Goes Wrong
When incidents happen, silence or confusion causes more damage than the breach itself. A good plan outlines exactly what to do and who takes the lead.
- Define roles: who investigates, who communicates, who reports.
- Set timelines for internal and external responses.
- Prepare draft templates for client communication or media statements.
2. Be Transparent with Clients and Partners
Hiding incidents or delaying communication often leads to frustration and loss of confidence. If you handle the situation clearly and honestly, people are far more likely to stay with you.
- Notify affected parties quickly, even if all details aren’t known yet.
- Share only verified information, never speculate.
- Offer a support channel to answer questions and guide next steps.
3. Protect Internal Trust as Well
Reputation matters inside your company, too. If employees feel exposed, misinformed, or blamed, it can hurt morale and engagement.
- Communicate openly during and after incidents.
- Turn events into learning opportunities, not punishment.
- Involve team leaders in building a culture of shared responsibility.
Prevent Attacks by Making Access Difficult from the Start
Cybersecurity doesn’t have to be perfect to be effective: it must make it hard enough that attackers give up and move on. Most businesses aren’t attacked because someone wants to attack them, but because they’re easy to reach. A weak password, an outdated system, or an improperly trained team member is often enough.
If your company works in the crypto space or manages digital assets, it’s important to go one step further. At Cryptoscam Defense Network, we support businesses and users with knowledge and resources focused on fraud detection, scam awareness, and safer online practices.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.
Frequently Asked Questions (FAQs) About Practices to Protect Confidential Company Information from Hackers
How often should I update my company’s cybersecurity plan?
You should review your cybersecurity plan every 3 to 6 months. Focus on changes in your tools, team structures, and workflows. If your company starts using new platforms, expands to new markets, or adopts additional technologies, update your policies accordingly to keep them effective and up to date.
What are the main cybersecurity risks for business owners in 2025?
The main cybersecurity risks for business owners in 2025 are:
- Advanced phishing attacks and AI-powered malware.
- Ransomware-as-a-Service (RaaS) is offered on the dark web.
- Insider threats and poor password hygiene across teams and departments.
What’s the role of employee training in cybersecurity?
Training helps reduce human error, which is one of the most common causes of breaches. A well-informed team can recognize phishing, avoid risky behavior, and report issues early, before they turn into bigger problems.
Photo via Freepik.





