Unauthorized transactions and fraudulent use of your identity can get out of control quickly, especially if the attacker gains access to a high-risk wallet linked to your funds. That’s why account takeover fraud solutions are now one of the most common things people search for when they rely on digital services.
The FTC reported that these incidents caused losses above USD 12 billion in 2024. In this post, we’ll guide you through steps you can apply at any moment, like security updates that help upgrade your accounts, routine activity checks, and steps that stop others from getting into your personal accounts.
Need support after a scam? Join our community today.
Best Account Takeover Fraud Solutions in 2025
When someone you don’t know gains access to your email, social media, or exchange accounts, your personal information becomes vulnerable, and your privacy is at risk. Here’s a list of the best account takeover fraud solutions to help you stay protected.
1. Activate Strong Authentication (MFA) on All Your Accounts
Multi-factor authentication (MFA) adds another confirmation step before allowing access. It works through a mix of something you know (your password), something you have (a one-time code or an authenticator app), or something linked to you (biometrics).
This added check can stop unwanted access, even in cases where your password has been exposed.
How to Apply it
- Turn on MFA in your email from the security settings.
- For banking apps, use in-app codes instead of SMS.
- Add external authenticators, like Google Authenticator or Microsoft Authenticator.
- In your social platforms, open the security section and activate a second verification step.
Example
Imagine someone trying to enter your email from a location that has nothing to do with your usual activity. Even if they manage to get your password, they won’t get any further because the authenticator app on your phone generates a unique code that only you can approve. That single requirement is enough to stop the attempt.
2. Use a Password Manager and Unique Credentials
A password manager helps you create and store strong credentials that are harder to guess during unwanted access attacks. This practice fits naturally within account takeover fraud solutions because it helps protect you when large data leaks reveal reused passwords.
How to apply it
- Select a trusted option such as 1Password, Bitwarden, or Dashlane.
- Use long and unique passwords for every platform.
- Allow the manager to generate them so you avoid predictable patterns.
- Replace any password involved in a recent breach.
Example
Picture an online store dealing with a breach where your password appears in the leaked file. If you used that same password in your email or mobile banking app, someone could try it until it works. With a password manager, each account uses a different login, preventing a single leak from turning into access to other services.
According to the report Psychology of Passwords 2024 by LastPass, 65% of users reuse passwords, which makes credential stuffing attacks much easier to do.
3. Monitor Sign-Ins and Connected Devices
Checking your active sessions helps you spot logins that aren’t yours, since Google, Apple, and Microsoft show your recent devices, and any unfamiliar one deserves attention. This habit also reduces the chance of getting caught in domain-network invoice scams, where attackers try to use your account details.
How to Apply it
- Check your recent login locations
- Check devices currently connected
- Check password changes you didn’t request
Example
Imagine opening your email’s security panel and noticing a login from a device you don’t recognize. Even if the session looks inactive, it could show that someone tried to get in. Ending the session remotely and creating a new password gives you control again and stops the attempt before it turns into access you never approved.
Have questions about dealing with scams? Contact us for support.
4. Set Up Security Alerts for Banking and Essential Services
Security alerts help you notice activity that doesn’t fit the way you typically use your accounts. Most banks offer notifications for purchases, transfers, or updates to personal details, giving you a chance to respond when something unexpected happens.
How to Apply it
- Turn on alerts for charges, transfers, and password changes.
- Choose in-app notifications instead of SMS.
- Check your recent activity at least once a week.
Example
Imagine receiving an alert about a transfer you never approved. That notification gives you a moment to sign in, freeze the account, and contact support before the situation grows. These alerts act as an early signal when something doesn’t align with your usual activity.
5. Apply Identity Theft Prevention Strategies in Your Daily Activities
Your everyday habits shape how exposed you are to unwanted access attacks. These identity theft prevention strategies work as part of stronger account takeover fraud solutions, helping you control what you share, what you approve, and the type of messages you trust.
How to Apply it
- Avoid sharing personal details on social platforms, such as addresses, contact numbers, or documents.
- Skip forms that request information that isn’t necessary for the service offered.
- Look at who is sending each email before opening it or downloading attachments.
- Use anti-phishing filters in your inbox to reduce exposure to messages that imitate legitimate companies.
Example
Imagine you see a form offering a big discount, but it asks for your ID number and a photo. With the right identity theft prevention habits in place, you’d pause, think it through, realize it seems risky, and choose not to share sensitive details that could later be used to access your accounts.
6. Strengthen Online Account Security on Social Networks and Work Platforms
Your personal and work profiles often give attackers enough clues to try accessing other services linked to you. Adjusting your online account security on platforms like LinkedIn, Meta, TikTok, or X helps prevent someone from using those accounts as an entry point to more sensitive information.
How to Apply it
- Limit who can view your contact details or job information.
- Remove permissions from apps you don’t use or don’t recognize.
- Turn on login approval to make sure each access request needs your confirmation.
- Check active devices regularly and sign out of sessions you didn’t start.
Example
Imagine someone browsing your LinkedIn profile and finding your work email visible to anyone. That small detail can be used to try logging into your company account. When you adjust your online account security, hide sensitive data, and activate login approval, any attempt is stopped before it affects you.
7. Use Fraud Detection Tools to Identify Unusual Activity
A fraud detection tool analyzes your digital habits and compares them with the way you usually interact with your accounts. These systems review your typical schedule, the devices you use, and the type of actions you perform.
With that information, they detect access attempts or changes that are different from what you normally do.
How to Apply it
- Turn on alerts that notify you when someone tries to log in at times you never use.
- Set monitoring for sensitive data such as email addresses, contact numbers, and recovery information.
- Choose tools that block fast, repetitive patterns associated with automated attacks.
- Review the activity summaries these systems generate so you can notice variations in your usual behavior.
Example
A user opens the security panel of one of their accounts and sees repeated login attempts from another country within very short intervals. The system also recorded an attempt to modify personal details. With that alert, the user updates credentials, closes active sessions, and stops the attempt before it progresses.
8. Review Activity from Apps Connected to Your Accounts
Most platforms keep a list of connected apps that can read your data and make changes. Reviewing these permissions helps you spot access that you no longer need or activity that could support an account takeover attempt. This step complements account takeover fraud solutions and keeps your information under closer control.
How to apply it
- Remove access from older apps or ones you no longer use.
- Check which apps have read-and-write permissions to avoid unwanted changes.
- Delete third-party connections you don’t recognize.
- Look at your security panel regularly to see if new connections appear.
Example
During a quick check, a user spots an unfamiliar app with read-and-write access. With that kind of permission, the app could modify information without warning. Once the user removes it and updates their password, any active session tied to that app gets cut off, and the chance of an unauthorized login goes down.
9. Protect Your Email as Your “Master Key”
Your email is the place where you recover access to your accounts, which makes it an easy target. If someone has access, they can reset passwords or create rules that move your messages without your consent.
It can also expose you to blackmail email scams, where attackers look for personal details to pressure you later.
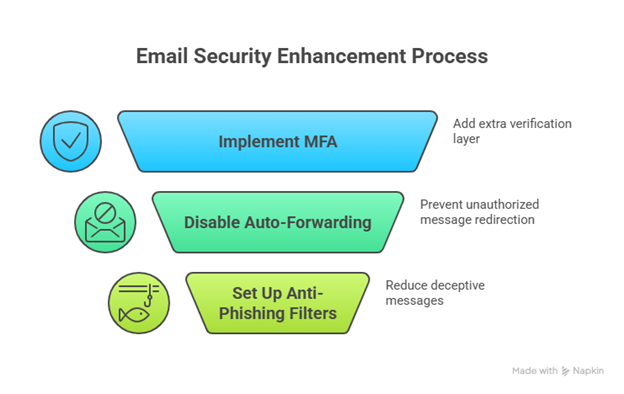
How to Apply it
- Use MFA to include an extra verification step.
- Turn off automatic forwarding when you don’t need it.
- Set up anti-phishing filters to reduce deceptive messages.
Example
During a routine check, you might notice a forwarding rule sending your emails to an unfamiliar address. That small detail could let someone receive verification codes meant for you. You remove the rule, change your password, activate MFA, and just like that, you stop the intrusion before it goes any further.
10. Use Secure Networks and Avoid Public Wi-Fi for Sensitive Services
Open networks make it easier for someone to intercept your sessions without you noticing. When you connect to public Wi-Fi to access banking or work platforms, your activity can be exposed. Choosing safer connections supports your account takeover fraud solutions and helps you reduce the chance of unauthorized access.
How to Apply it
- Avoid public Wi-Fi when you need to access banking or work services.
- Switch to mobile data whenever you handle information that matters to you.
- Use private networks you trust and that require a password.
Example
During a trip, someone tries to log in to their digital banking using the airport’s Wi-Fi. The page looks familiar, but the network allows a third party to view the session. After disconnecting, switching to mobile data, and updating the password later, the person prevents their information from being exposed.
Stop Account Takeover Fraud With Smarter Habits
Sometimes, checking your digital activity helps you notice how much of your security depends on habits that tend to be ignored. Account takeover fraud solutions work when you apply them with consistency, and every small adjustment changes the way you respond to access attacks that don’t follow your usual digital habits.
At Cryptoscam Defense Network, we share resources that guide you through each step so you can keep your accounts protected. If you want to move on with more confidence, learn how to report a deepfake, another type of threat that can affect your identity.
✅ Download our Fraud Report Toolkit to easily collect, organize, and report scam cases, with dropdowns for scam types, payment methods, platforms, and direct links to agencies like the FTC, FBI, IC3, CFPB, BBB, and more.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.







