A digital wallet stores your payment information and facilitates electronic transactions, similar to a physical wallet but online. However, these wallets are susceptible to risks. In fact, in 2024, a notable pattern was observed in the transfer of stolen funds through such services, as reported by Chainalysis.
These platforms hide the origins of the stolen funds, complicating the process for authorities to track and recover them. In this post, we will explore what is a high-risk wallet and why it is important in the crypto world. You will also discover the most common risks linked to digital wallets and simple tips to improve wallet security.
Need support after a scam? Join our community today.
What Is a High-Risk Wallet?
A high-risk wallet is a financial account or digital wallet that is more likely to face security challenges such as fraud or unauthorized access. This classification is often due to the wallet’s use, which exposes it to increased security risks, such as storing large sums of money or participating in high-risk transactions. These wallets include:
1. Hot Wallets
Hot wallets, such as MetaMask or browser-based wallets, are constantly connected to the Internet, which allows transactions to be fast and immediate. They are ideal for daily transactions due to their accessibility and ease of use.
Why Hot Wallets Are Considered High-Risk
- Constant internet connection: Their continuous online status makes them vulnerable to hacking attempts and malware.
- Exposure to phishing attacks: Users can be tricked into sharing sensitive information through fake websites or emails.
- Lower control over private keys: If the private key is compromised, hackers can easily access and transfer funds.
- Third-party dependencies: Some hot wallets rely on external platforms, increasing exposure if those services are attacked.
2. Hardware Wallets
Hardware wallets, like Ledger Nano S, store private keys offline, providing a higher level of protection compared to hot wallets. They are commonly used for long-term storage of cryptocurrencies because they offer greater control over digital assets.
Why Hardware Wallets Are Considered High-Risk
- Physical theft or loss: If someone gains physical access to the wallet, they can control all the stored assets.
- Firmware vulnerabilities: Outdated or unpatched firmware can expose the wallet to security flaws.
- User dependency: The security of the wallet depends entirely on how well the user maintains it (e.g., firmware updates, proper storage).
- Backup risks: If recovery phrases or backup details are not stored securely, they can be exploited to gain access to funds.

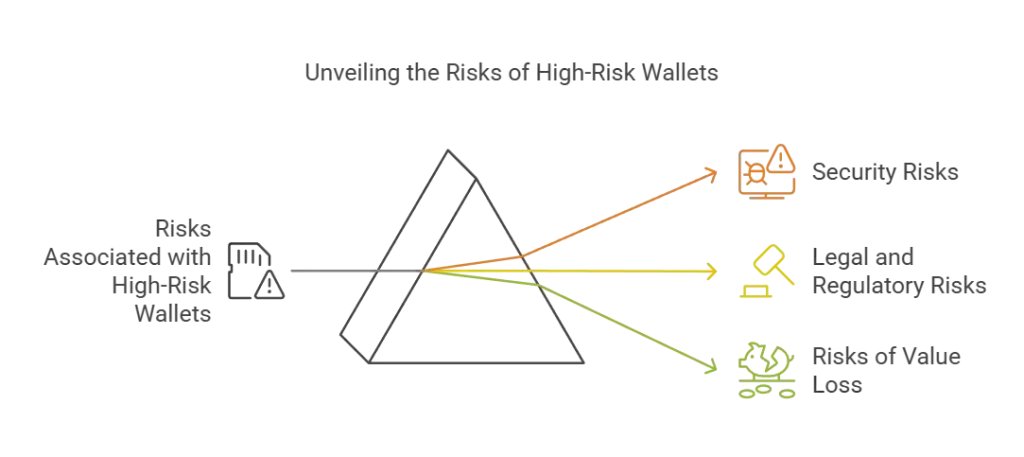
What are the Risks Associated with High-Risk Digital Wallets?
High-risk wallets, while functional and innovative, come with risks that users must understand to protect their digital assets effectively. These risks are related to:
1. Security Risks
High-risk wallets, particularly those connected to the Internet (hot wallets), are vulnerable to multiple types of cyber threats. These include hacking, where attackers gain unauthorized access to wallet data, and phishing attacks, where users are tricked into providing sensitive information through fraudulent emails or fake websites.
For example, a user might receive an email that appears to be from a legitimate wallet provider, requesting them to verify their credentials. Clicking on the link and sharing their details would give hackers full access to their wallet and funds.
2. Legal and Regulatory Risks
While not tied directly to high-risk wallets themselves, the platforms on which they operate can impact their risk profile. Regulatory changes and compliance requirements can affect how these wallets are used and managed.
For example, shifts in policy regarding digital payments can introduce new compliance obligations or restrict certain types of transactions.
3. Risks of Value Loss
High-risk wallets that are frequently used for transactions, such as shopping or trading, can expose users to potential financial loss through fraud or theft. If a wallet is compromised, the user may lose funds stored or transacted without any easy recourse for recovery.
For example, if a trader uses a hot wallet to process daily transactions on an exchange and the wallet is hacked, all assets could be transferred instantly without the possibility of recovery.
How High-Risk Wallets Are Used in Digital Fraud?
High-risk wallets are commonly exploited in various fraud schemes due to their digital nature and the anonymity they provide. Common scams include investment schemes where fraudsters promise high returns, and tech support scams, where victims are tricked into believing they need to pay for unnecessary services.
For example:
1. Investment Scams using Digital Wallets
- Fraudsters may show fake profit reports to convince victims to transfer funds from their digital wallets into fraudulent investment platforms.
- Victims later discover they cannot withdraw the funds from their digital wallets.
2. Tech Support Scams using Digital Wallets
- Victims receive fake alerts on their devices, claiming that their digital wallets have been compromised or require urgent updates.
- These alerts instruct them to make payments from their digital wallets to resolve non-existent issues, leading to unauthorized fund transfers.
Have questions about dealing with scams? Contact us for support.
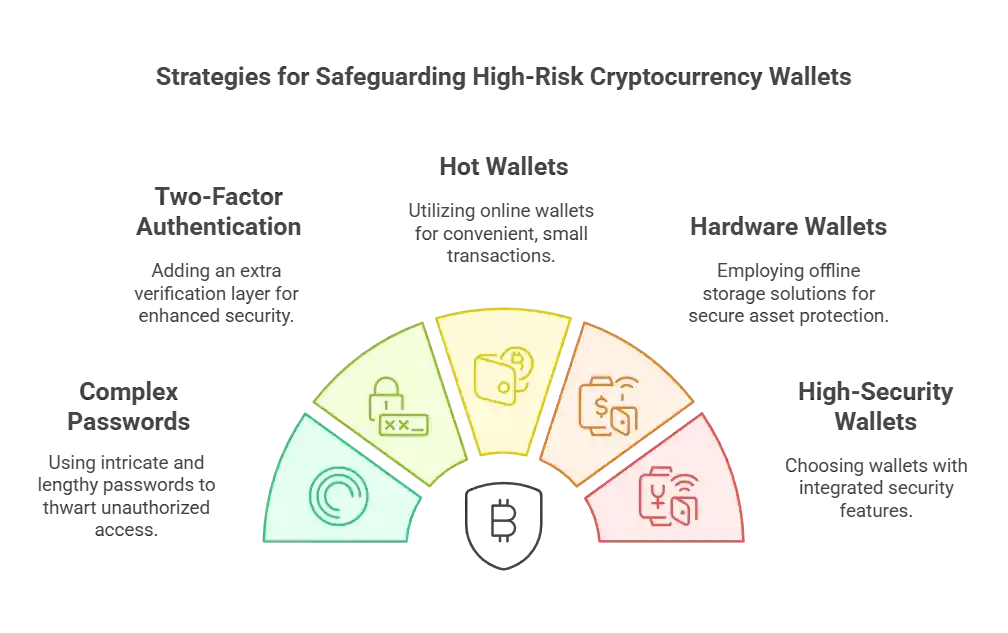
Tips for Protecting Yourself When Using High-Risk Wallets
Now that you understand what a high-risk wallet is, and the risks associated with it, it’s important to learn strategies to protect your cryptocurrencies or digital assets. Follow these tips to reduce the potential threats to your digital wallet:
1. Use Strong and Unique Passwords
Use complex passwords that include a mix of letters, numbers, and symbols and extend beyond 16 characters to improve their effectiveness. This combination creates a shield against brute force attacks, reducing the risk of unauthorized access to your digital assets.
2. Add Extra Protection with Two-Factor Authentication
Using two-factor authentication offers an essential second layer of security, requiring a secondary code or device verification in addition to your password. This method reduces the chance of unauthorized access, even if your main password is compromised.
3. Use Hot Wallets for Everyday Transactions
For daily transactions, use hot wallets that, while connected to the internet and more convenient, hold smaller sums due to their increased vulnerability. These wallets offer quick access and easy management of funds, making them ideal for frequent, smaller transactions.
4. Keep Your Assets Safe with Hardware Wallets
Consider using tools and services designed to protect your assets. Hardware wallets, like the Ledger Nano X and Trezor Model T, are excellent choices for storing cryptocurrency they keep your keys offline and are specifically designed to fight interference.
5. Choose Wallets That Work with Hardware Options
Choosing wallets that prioritize security features, such as Exodus or Trust Wallet, can increase your protective measures. These digital wallets also come with hardware wallets, adding an extra layer of security for your digital assets.
Take Control: Protect Your Assets from Threats with CDN
Learning what is a high-risk wallet is a task every user should take seriously. It doesn’t matter if you use digital wallets frequently, for saving purposes, or if you’re just considering using one — knowing how they work and the challenges they face is key to keeping your assets safe.
Even these wallets come with security measures, especially due to their vulnerability to cyber-attacks and fraud schemes. At Cryptoscam Defense Network (CDN), we provide the best tool to protect your digital assets: knowledge and basic protection tips to help you avoid potential breaches.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future frauds.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Frequently Asked Questions (FAQs) about High-Risk Wallets
What Should I Do If My Hardware Wallet is Stolen or Lost?
If you lose your hardware wallet, or it is stolen, the first thing you should do is acquire a new hardware wallet and use your recovery seed to restore your assets on the new device. Make sure to back up the new recovery seed and, if possible, move your assets to a new seed for added protection.
How Can I Check If the Firmware of my Hardware Wallet is Up to Date?
Visit the manufacturer’s official website and follow the specific instructions for your device model to check and update its firmware. Manufacturers like Ledger and Trezor offer step-by-step guides for firmware updates, making sure your device is protected against the latest known vulnerabilities.
How Can I Identify and Avoid Fraudulent or Phishing Websites that try to Steal Information from my Wallet?
To identify and avoid fraudulent or phishing websites, it is important to carefully examine emails and websites requesting personal or financial information. You can:
- Check the website’s URL, looking for security signs such as the HTTPS lock in the address bar.
- Avoid clicking on suspicious links or downloading files from unknown sources.
- Use web security tools and browser extensions that help identify potentially dangerous websites.
Photo via Freepik.