Connecting to a Wi-Fi network may seem harmless, but wifi hackers can turn even the most casual access point into an opportunity for stealing personal information. According to Cobalt, 81% of tested WiFi networks are completely vulnerable to attacks.
With only a basic app and a simple device, anyone can start hacking unsecured networks or intercept passwords from nearby connections. In this post, we’ll explain how these wifi hackers operate, the most common hacking methods, early warning signs, and how to protect yourself in everyday situations.
Need support after a scam? Join our community today.
What is a WiFi Hacker?
Wifi hackers are people who use unauthorized digital methods to access private wireless networks without permission. Most don’t rely on expensive tools: a standard laptop and free software are often enough to start scanning and exploiting open or poorly configured networks.
Their goal is to find cracks in your network setup and get in without detection. These breaches may affect personal environments, like a family home, or public spaces with shared WiFi. Once inside, they can monitor what’s being transmitted or, worse, take control of connected devices. There are generally two types of actors involved:
- Ethical hackers: who are hired to uncover security issues and report them.
- Black-hat hackers: who pursue unauthorized access for personal or illegal gain.
One example is frequently seen in airports or shopping centers, where a malicious user sets up a fake network that copies the official one. As soon as someone connects, thinking it’s safe, their private traffic can be monitored or stolen.
📊 According to Checkpoint, 24% of devices connected to public networks have already been exposed to interception attacks. This is more common than many people realize and entirely preventable.
Who Are WiFi Hackers and What Motivates Them?
WiFi hackers don’t always share the same motivations. Some are curious, others want financial gain, and a few just want to test how far they can go. What connects them is their ability to find weaknesses in wireless networks and use that access to reach private content.
Here’s a look at the most common types:
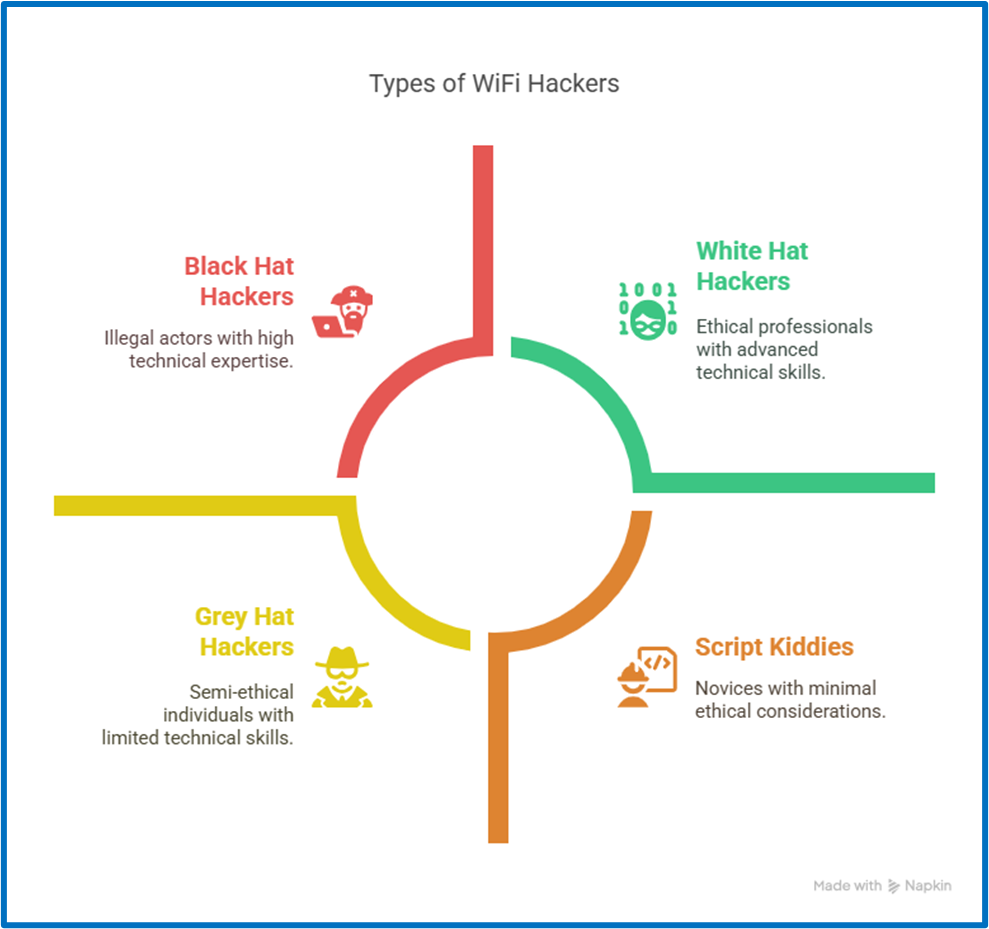
1. Black-Hat Hackers
These attackers use their technical skills for illegal activities. They may steal data, spread ransomware, or sell entry points to vulnerable networks. Some act alone, others form part of coordinated groups that work to obtain financial or reputational outcomes.
2. White-Hat Hackers
Often called ethical hackers, these professionals are invited to test systems and report any flaws they uncover. They’re part of security programs that reward proactive defense, and their goal is to reduce the risk of real threats created by wifi hackers.
3. Grey Hat Hackers
Their actions fall somewhere in between. They explore systems without permission and fix what they find—but without official approval, their work crosses a legal line. Picture someone who points out a flaw in a café’s WiFi, but never asked to access it in the first place.
4. Red Hat Hackers
Hired by institutions or security agencies, these hackers go after criminal attackers using their tools like malware, fake access points, or reverse engineering. They take a direct approach to shut down malicious groups and protect sensitive environments.
5. Hacktivists
These intruders are driven by causes. Their attacks often carry a message: protest, exposure, or digital disruption. One might gain access to a public agency’s WiFi to leak internal emails or publish controversial material.
6. Script Kiddies
They’re new to hacking, and they use tools built by others. They don’t fully realize how things work, but they try anyway, sometimes for fun, sometimes for attention. Their actions might seem chaotic, but the damage can be very real.
Knowing these profiles helps you stay alert and identify where potential threats may come from. If you manage sensitive data at home or work, it’s worth learning how to prepare for a cyberattack long before one reaches your network.
Have questions about dealing with scams? Contact us for support.
How Do WiFi Hackers Attack Networks?
WiFi hackers depend on various strategies to steal information, gain access to restricted networks, or disrupt connectivity. Some techniques are more common in public settings, while others are often used in home networks.
Here’s how these methods work and what they can compromise:
1. Man-in-the-Middle Attack
In this method, the wifi hacker quietly inserts themselves between your device and the legitimate network. Acting as an invisible middle layer, they can intercept, modify, or redirect the data flowing through the connection.
📍 Example: You’re at a café and connect to the free WiFi. Without your knowledge, someone nearby has set up a system to intercept that signal. As you check your email or shop online, the hacker is viewing every action in real time.
2. Brute Force Attack
This technique uses automated programs that try thousands of password combinations until one works. WiFi hackers use these tools to break into networks with weak credentials, often without needing any further interaction.
📍 Example: Someone installs password-cracking software and targets nearby routers. One network uses WPA2 and a simple password. The program runs all afternoon, and by evening, they’ve accessed the neighbor’s internet without raising any alerts.
3. Phishing Attack
Instead of using advanced tools, the attacker counts on social engineering and clone phishing. Once connected to a network, they push fake websites or login alerts that appear genuine, hoping the victim will enter sensitive details.
📍 Example: At a hotel, the WiFi asks you to log in “for security reasons.” You type your email and password. The page looks official, but it’s a copy created by the hacker to steal your information.
4. Evil Twin AP Attacks
The attacker creates a fake access point with the same name and setup as a real network. Victims connect to the fake one without noticing, and their activity is fully visible to the attacker.
📍 Example: In a café, you see two networks named “CafeConnection.” You pick one at random, unaware it belongs to a hacker. As you browse or log into your accounts, they capture every detail.
5. Replay Attack
Here, the attacker records a valid data transmission and uses it again to trigger a repeated action. Although the content isn’t changed, the copied request is treated as if it were legitimate.
📍 Example: Someone captures the signal sent by a smartphone to unlock a smart door. Later, they replay that exact signal and open the door, no password required.
6. Packet Sniffing
Attackers scan the data packets moving across an unencrypted network. These can include login credentials, hacked emails, or browsing activity, all in a readable format.
📍 Example: While reading email on a public WiFi without HTTPS, a nearby hacker uses sniffing software to collect everything from your inbox to saved passwords.
7. Jamming Attacks
In this case, the goal is disruption. Hackers flood the same wireless frequency with noise, interrupting legitimate connections. The chaos may push users to switch to a malicious access point without realizing it.
📍 Example: During a business event, a team loses WiFi access repeatedly. While reconnecting, some attendees choose a similar-looking network that belongs to the attacker, unknowingly handing over their session data.
8. MAC Spoofing
Every device has a MAC address—a unique hardware identifier. The hacker clones the address of a trusted device to gain access to a restricted network.
📍 Example: A corporate network only allows approved devices. A hacker copies the MAC address of one of them and joins the network without being flagged as an intruder.
What Are the Signs That Someone Accessed Your WiFi?
When wifi hackers gain access to a network, they don’t always leave visible signs. Still, there are specific behaviors that could suggest something’s wrong and that it’s worth reviewing your router’s settings carefully. Some common signs are:
- Unrecognized devices connected to your network: If you check your router’s device list and see unfamiliar names or addresses, that could signal unauthorized access.
- Unusually slow connection speeds: If your internet becomes sluggish while no one else is using it, it might be due to someone else consuming your bandwidth.
- Changes in your router’s settings: Some attackers alter DNS configurations, disable firewalls, or modify login credentials.
- Suspicious activity on linked accounts: This includes login attempts from unfamiliar locations in services like social media, online banking, or streaming platforms.
How to Make Your WiFi Less Accessible to Hackers?
A poorly secured home network is often an easy target for wifi hackers. Many use automated tools that require little effort. Because of this, a few easy changes can greatly lower your exposure:
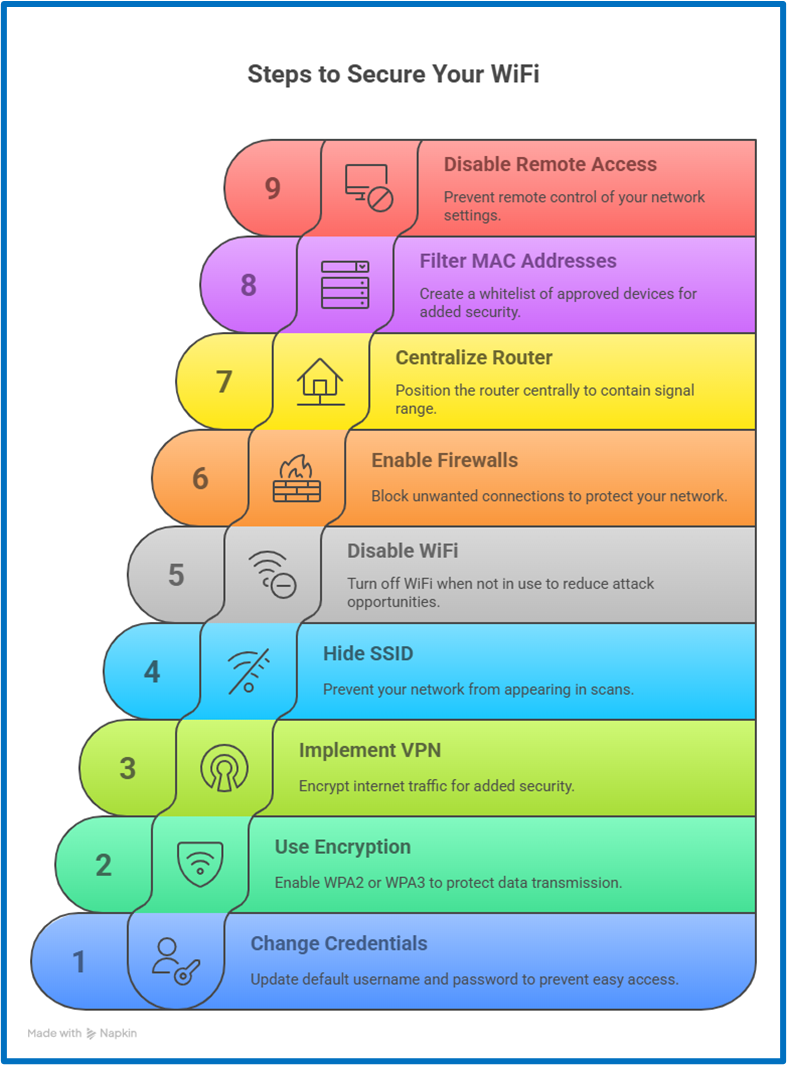
1. Change Your Router’s Default Username and Password
One of the most overlooked risks is keeping the manufacturer’s default credentials. These are widely known and often published online, making it easy for anyone nearby to gain access. Updating them should be your first step.
2. Use WPA2 or WPA3 Encryption
Encryption keeps your traffic private. If your network still uses WEP or is open, it becomes vulnerable to interception. WPA2 is acceptable, but if your router supports it, enable WPA3 for stronger resistance against modern attacks.
3. Use a VPN
A virtual private network encrypts your entire internet traffic, even on a secure network. If someone does break in, your information will still be protected. This is especially useful when working remotely or using public WiFi.
4. Hide Your SSID
Your SSID is the name of your network. By hiding it, you prevent it from showing up in automatic scans, making it harder for someone to connect unless they already know it. This adds an extra layer of privacy.
5. Turn Off WiFi When You’re Not Home
There’s no benefit to leaving your WiFi active when no one is using it. Shutting it down when you’re away reduces the window of opportunity for remote attacks, especially in buildings with dense wireless activity nearby.
6. Turn On Firewalls
Firewalls help you block unwanted connections. You can activate them both on your router and on individual devices. This stops intruders from freely exploring your network if they do manage to enter.
7. Place the Router at the Center of Your Home
Keeping your router near windows or outer walls increases the signal’s reach beyond your home. Positioning it centrally helps contain the range and distribute the signal more evenly indoors.
8. Filter Connections by MAC Address
Each device has a unique MAC address. You can create a whitelist of approved devices in your router’s settings. Although experienced attackers can bypass this, it still serves as an added barrier.
9. Restrict Remote Administration
Many routers allow access to their control panel over the internet. If you don’t need this function, turning it off prevents someone from trying to take control of your network from a distance.
Don’t Let WiFi Hackers Catch You Off Guard
These days, WiFi hackers don’t work in secret. They take advantage of simple oversights: a password left unchanged, a quick tap on a public network, or leaving your WiFi on when no one’s home. Learn the most common attack methods, improve your home setup, and stay alert while using WiFi in public.
At Cryptoscam Defense Network, we’re here to help you stay aware of digital threats. We guide you through spotting fake websites, recognizing early signs of crypto scams, and protecting your phone from risks like those explained in how to protect phone from hackers.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.







