When celebrities get hacked, the entire internet feels the impact. Private photos leaked, personal conversations exposed, social media accounts hijacked and used to send fake news or scams. We’ve all seen the headlines, glamorous names turned into warning tales.
However, the truth is that these digital breaches don’t just affect celebrities. They reveal how vulnerable we all are in a connected world, where a single weak password can open the door to chaos. In this post, we’ll explore the world of a celeb hacker, who they are, and most importantly, what you can do to avoid becoming a victim of similar cyberattacks.
Need support after a scam? Join our community today.
What Is a Celeb Hacker?
A celeb hacker is someone who targets public figures such as actors, musicians, influencers, and politicians to steal personal data, leak private content, or hijack their digital identities. These cybercriminals are often highly skilled and motivated by fame, financial benefits, or even ideological reasons.
What Techniques Do Hackers Use to Target Celebrities?
Even the most famous names in the world can fall victim to simple but powerful cyberattacks. What makes these incidents more dangerous is that the methods used aren’t exclusive to high-profile targets. They’re the same techniques hackers use on everyday users, just with higher stakes and visibility.
Here are the most commonly used by celebrity hackers:
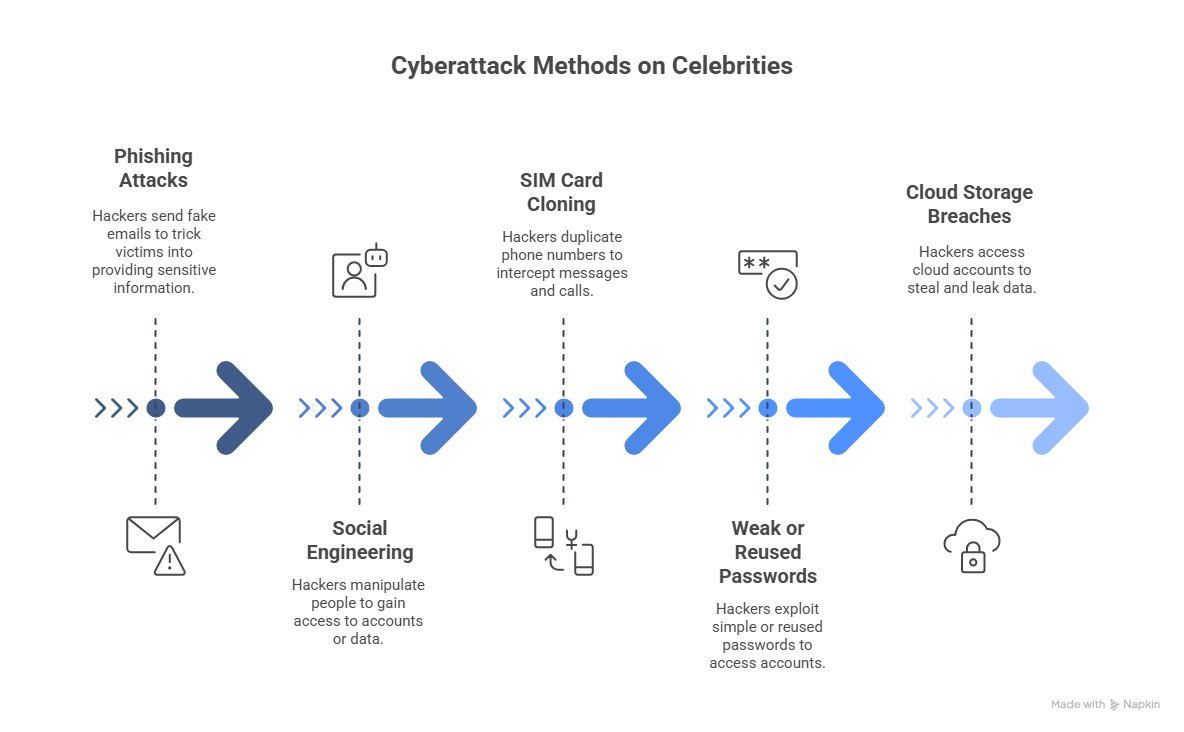
1. Phishing Attacks
Hackers send fake emails, texts, or DMs that appear to come from trusted companies or people. The goal is to trick the victim into clicking a link or sharing sensitive information.
How Does it Work?
A celebrity receives an email that appears to be from Apple or Instagram, asking them to verify their account. They click the link, enter their login info, and accidentally hand over access to the hacker. These messages look official, use urgent language, and take advantage of the victim’s trust in well-known platforms.
2. Social Engineering
Social engineering is about manipulating people instead of systems. Hackers collect personal information and use it to trick their way into protected accounts or data.
How Does it Work?
A hacker pretends to be a celebrity’s assistant or tech support agent and calls a mobile provider to reset account access. They use public interviews or social media posts to answer security questions. It is dependent on human error and trust, especially when celebrities delegate account access to teams or assistants.
3. SIM Card Cloning
Hackers duplicate the target’s phone number by convincing a mobile provider to activate a new SIM card. Once cloned, they can receive text messages and calls meant for the victim.
How Does it Work?
The hacker receives all two-factor authentication codes sent via SMS and uses them to reset passwords for social media, email, and cloud storage accounts. Mobile providers can be tricked into verifying fake identities. Without app-based 2FA, SMS can be a weak point.
4. Weak or Reused Passwords
Many celebrities, like most people, use simple passwords or keep the same ones across platforms. This makes it easier for hackers to break into multiple accounts.
How Does it Work?
A leaked password from one platform, like an old email or fan club login, is tested on more sensitive services like iCloud or Instagram. If reused, it opens all doors. It only takes one data breach for a password to be exposed. Reusing it multiplies the risk.
5. Cloud Storage Breaches
Services like iCloud, Dropbox, or Google Drive automatically back up photos, videos, notes, and more. If login credentials are stolen, the hacker gains access to everything stored there.
How Does it Work?
Hackers access a celebrity’s cloud account, download private photos and videos, and leak them online or sell them. Most people don’t enable two-factor authentication or check cloud security settings regularly.
Have questions about dealing with scams? Contact us for support.
How Celeb Hackers’ Threats Extend to Everyone Online?
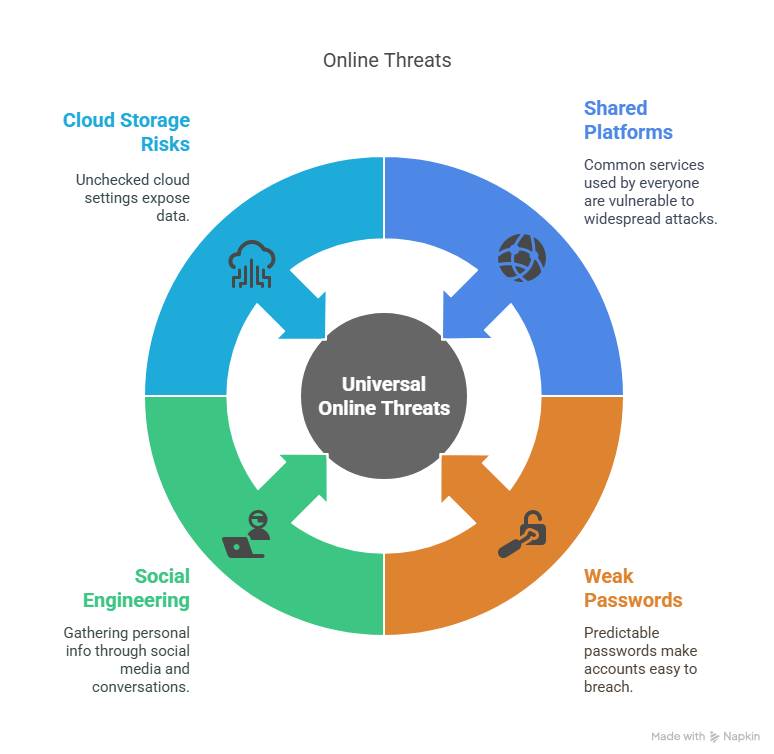
Celebrity hacks might get headlines, but the same methods used to breach their accounts are actively being used against everyday people. Many of the vulnerabilities used in celeb hacks are even more common among regular users. Here’s how these threats affect all of us:
1. We All Use the Same Platforms
Whether you’re Beyoncé or a college student, your accounts are likely hosted on digital platforms like iCloud, Instagram, Gmail, or WhatsApp. Once hackers learn a method, they apply it globally. If phishing works on a celebrity, it’ll work on anyone not trained to spot a fake login page or suspicious email.
2. Password Habits Are a Universal Weakness
Weak, reused, or predictable passwords are one of the easiest ways hackers gain access, and this habit doesn’t discriminate by fame. If you use your dog’s name or your birthdate across multiple accounts, you’re just as vulnerable as a celebrity doing the same.
3. Social Engineering Isn’t Just for the Famous
Hackers get personal information through social media, online forms, or even casual conversations. If your privacy settings are open or you overshare online, you’re a potential target. Protect your social media accounts from hackers by limiting what you share publicly or using strong passwords.
4. Cloud Storage and App Permissions Represent Daily Risks
Most users don’t review their cloud backup settings or remove unused app permissions. Hackers use this to access private content through forgotten or outdated connections. Just like with celebrities, your data can be sitting exposed in a cloud service you rarely check.
Celebrity Hacking Cases You Should Know About
Celebrity hacks have become modern scandals, shaking the public and exposing just how fragile digital privacy can be. These high-profile cases highlight not only the techniques hackers use but also the lasting consequences of a successful attack.
Here are some of the most controversial celebrity hacking incidents:
1. The Fappening, also known as Celebgate
According to the BBC, in 2014, private photos of over 100 celebrities were leaked online after hackers accessed their iCloud accounts through phishing and weak security questions.
Hackers used phishing emails to trick victims into giving away their Apple ID credentials. Once inside, they downloaded years’ worth of personal photos and videos. This case started global debates about cloud security, digital consent, and the treatment of women in media. It has been one of the longest and most damaging leaks to date.
2. Matthew Perry’s Twitter Hijacking
As reported by Bitdefender, the late actor Matthew Perry’s official Twitter was briefly taken over by scammers asking for cryptocurrency donations. The account posted solicitations for crypto donations, claiming to support addiction recovery efforts.
This shows how social engineering or malware can hijack accounts, even after a celebrity’s death, making it a warning tale for legacy security. Scams on X (Twitter) often use emotional causes and trusted identities to trick followers into sending money or revealing personal information.
3. Tina Knowles’ Instagram Like Incident
According to the New York Post, Beyoncé’s mother, Tina Knowles, revealed her Instagram was hacked after her account “liked” a post about Jay‑Z raping allegations.
An unauthorized interaction on her profile sparked concern and required official denial from Knowles. Even simple actions, like a “like”, can damage reputations and force public statements to clear up confusion.
How Can You Protect Yourself from Celeb Hackers?
You do not have to be a public figure to become a target. Anyone who wants to keep their digital life safe must follow smart cybersecurity habits. The good news is, you don’t need to be a tech expert to defend yourself. A few simple changes can go a long way.
Here are practical steps anyone can take to stay secure:
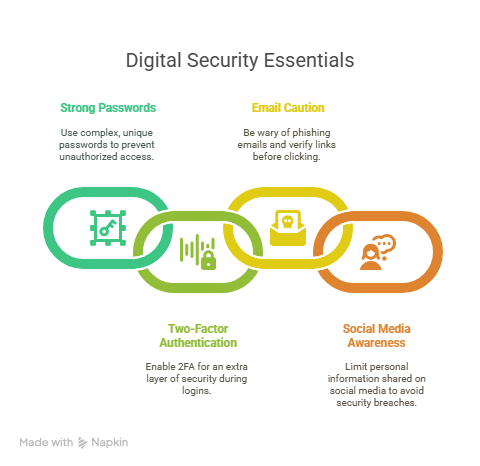
- Use strong, unique passwords: Avoid obvious choices like birthdays or pet names. Use a mix of letters, numbers, and symbols. Most importantly, don’t reuse passwords across accounts.
- Enable Two-Factor Authentication (2FA): Adding a second step to logins makes it much harder for hackers to gain access, even if they have your password. Use app-based 2FA like Google Authenticator instead of SMS to prevent SIM card cloning.
- Be cautious with emails and links: Phishing is everywhere. Don’t click on unexpected links, even if the message looks official. Always check the sender’s address and tap over links to preview the URL before clicking. If in doubt, go to the website directly instead of through email.
- Don’t publish too much on Social Media: The more personal information you post, the easier it becomes to guess passwords or security questions. Think twice before sharing birthdates, locations, or family names. Keep your profiles private when possible.
Cybersecurity Isn’t Just for Celebrities—It Starts with You
You do not need to be famous to attract the attention of a celeb hacker. All it takes is one email address, a cloud account, and a weak password. Fortunately, you do not need a full security team to protect yourself. With a few smart digital habits and increased awareness, you can take back control of your online identity.
If you recognize any of these scenarios, at Cryptoscam Defense Network, we offer the knowledge and support you need to fight against online fraud, promote safer cryptocurrency use, and stay informed through real-time cybersecurity prevention.
We Want to Hear From You!
Fraud recovery is hard, but you don’t have to do it alone. Our community is here to help you share, learn, and protect yourself from future fraud.
Why Join Us?
- Community support: Share your experiences with people who understand.
- Useful resources: Learn from our tools and guides to prevent fraud.
- Safe space: A welcoming place to share your story and receive support.
Find the help you need. Join our Facebook group or contact us directly.
Be a part of the change. Your story matters.
Frequently Asked Questions (FAQs) About Celeb Hackers
Why Do Hackers Go After Celebrities?
Because celebrities have valuable digital assets and massive online exposure. A single leaked photo or hacked tweet can generate huge media attention, making them prime targets.
Can Regularly People Be Hacked The Same Way?
Absolutely. The same techniques used on celebrities, like phishing, SIM swapping, and weak passwords, are also used on everyday users. Hackers look for vulnerabilities, not fame.
What Should I Do If I Think My Account Has Been Hacked?
Immediately change your passwords, enable two-factor authentication, and review any recent account activity. If you use the same password on multiple sites, update those too.
Photos via Freepik.





